Data encryption is a critical element of modern cybersecurity that helps protect sensitive data from unauthorized access. According to a report by Cybersecurity Ventures, global cybercrime costs are expected to reach $10.5 trillion annually by 2025, highlighting the importance of robust encryption methods. Encryption ensures that even if data is intercepted, the encrypted data cannot be read without the correct decryption key. This article will discuss key encryption methods such as symmetric and asymmetric encryption and their practical use cases in industries such as healthcare, finance, and cloud computing. Additionally, we will cover best practices that help companies successfully implement encryption and strengthen their data security posture.
What is Data Encryption?
Data encryption is the process of converting readable plaintext or data into ciphertext that can only be opened by someone with the appropriate decryption key. This process ensures that sensitive data remains confidential even if unauthorized individuals obtain it. Encryption is widely used in various applications, from protecting personal communications to protecting data in transit or stored in databases, servers, and cloud storage systems.
The Importance of Data Encryption
In today’s digital world with cyberattacks on the rise, protecting sensitive information from unauthorized access is essential. Data encryption ensures that encrypted data remains confidential, secure, and private, whether stored on devices, transmitted over networks, or processed in the cloud. By protecting sensitive information, organizations can comply with regulations, minimize the risk of data leakage, and maintain customer trust.
How to Encrypt Data?
Data encryption occurs using an algorithm (cipher) and a key to convert plaintext into ciphertext. This is possible using hardware or software solutions. Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses public and private keys. Encryption tools such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are widely used to protect sensitive information.
In the following sections, we will examine the methods and corresponding algorithms for data encryption in more detail.
Data Encryption Methods and Algorithms
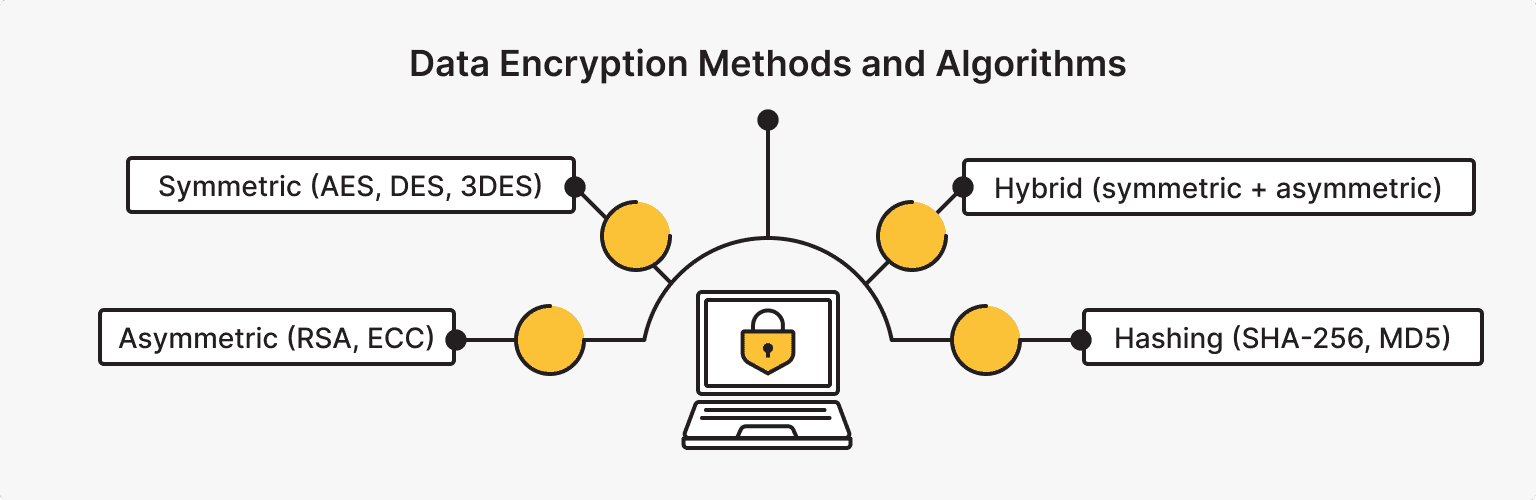
Modern encryption methods are divided into four main data encryption types:
- Symmetric
- Asymmetric
- Hashing
- Hybrid
Each type of data encryption includes the use of standard algorithms.
Symmetric Data Encryption (AES, DES, 3DES)
Symmetric encryption uses a single key for encryption and decryption, making it fast and efficient for large amounts of data. Symmetric encryption includes common algorithms such as AES (Advanced Encryption Standard), DES (Data Encryption Standard), and 3DES (Triple DES). AES is the most widely used due to its high security and speed, while DES and 3DES are considered less secure and deprecated, mainly in favor of AES.
Asymmetric Data Encryption (RSA, ECC)
Asymmetric encryption uses a public key for encryption and a private key for decryption. This division of keys increases security. Asymmetric encryption includes standard algorithms such as RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography). While RSA is widely used to protect digital signatures and data transfer, ECC provides the same security with smaller key sizes, making it faster and more efficient for mobile and IoT devices.
This is the ideal solution for large-scale projects, offering unbeatable protection, high performance, and flexible settings.
Hashing (SHA-256, MD5)
Hashing transforms data into a string of characters of a specific size different from the input data. Unlike encryption, hashing is a one-way process and cannot be reversed. This method includes SHA-256 (Secure Hash Algorithm), which is widely used for secure hashing, especially in blockchain technologies, and MD5 (Message Digest 5), which has become outdated due to vulnerabilities. Hashing is primarily used to store passwords and digital signatures and to verify data integrity.
Hybrid Data Encryption Methods
Hybrid encryption combines symmetric and asymmetric encryption to leverage the strength of each method. It is widely used to exchange asymmetric encryption (such as RSA) for secure key exchange with symmetric encryption (such as AES). This method provides the security of asymmetric encryption for key exchange while maintaining the speed and efficiency of symmetric encryption for data transfer. This method of data encryption is a standard component of the SSL/TLS protocols.
Data Encryption Use Cases

In this section, we will introduce you to various use cases of encryption, from encryption for cloud storage to encryption for IoT devices. These examples demonstrate how data encryption improves security in multiple environments and applications.
- Cloud Storage Encryption
Encrypting data on remote servers protects against unauthorized access, whether the servers are at rest or in transit. While cloud service providers often offer encryption, organizations should implement their own to maintain data privacy and control over the encryption keys.
- Data at Rest and Data in Transit Encryption
Data in transit refers to data moving across networks, while data at rest refers to data stored on devices or servers. Encrypting data at rest protects data from physical theft or unauthorized access, while encrypting data in transit prevents interception or tampering with data in transit.
- Email and Message Encryption
Email and message encryption protects sensitive messages from being stolen or accessed by unauthorized parties. Encryption methods such as PGP (Pretty Good Privacy) or end-to-end encryption in messaging apps ensure that only the intended recipients can read the content, protecting personal and business information from cyber threats.
- Database and File Encryption
Database and file encryption ensures that sensitive data remains protected even if the storage system is compromised. This is especially important for financial data, medical records, and intellectual property. TDE (Transparent Data Encryption) and file-level encryption tools help protect structured and unstructured data from unauthorized access.
- IoT Devices and Encryption
IoT device encryption is critical to protecting data from theft or misuse, as IoT devices collect and transmit vast amounts of sensitive information. It encrypts sensitive data such as personal health records, smart home device data, and industrial IoT sensor readings while ensuring secure communication between devices and cloud services.
Tools and Technologies for Data Encryption

Data encryption requires robust tools and technologies to ensure security across various environments and use cases. The following sections describe popular software, hardware, and cloud solutions for effective data encryption.
Popular Data Encryption Software and Libraries
The following encryption programs and libraries are widely used to protect data:
- OpenSSL is a famous group of open-source tools that offers strong cryptographic capabilities such as SSL/TLS encryption for secure communications.
- GnuPG (GPG) is another tool that uses encryption standards like PGP, which are helpful for encrypting files and secure email.
- Libsodium offers developers modern cryptographic features such as authenticated encryption and key management.
- VeraCrypt is widely used for disk encryption, providing additional protection for sensitive data.
Their flexible encryption capabilities make these libraries and tools suitable for developers and organizations using encryption across multiple platforms.
Hardware Data Encryption Solutions
Hardware encryption directly encrypts data using specialized hardware, reducing the risk of software vulnerabilities.
- Trusted Platform Modules (TPM) are modules found in computers that protect sensitive data, such as credentials and data encryption keys.
- Hardware Security Modules (HSM) are specialized devices that businesses use to manage and store cryptographic keys securely. These devices provide a tamper-proof environment for critical encryption tasks.
- Self-Encrypting Drives (SED) automatically encrypt data stored on hard drives, ensuring that data remains protected even when the drive is removed.
These devices provide effective and reliable encryption, especially for businesses with sensitive data.
Cloud Data Encryption Services
Cloud encryption services ensure secure storage and management of data in cloud environments. Encryption services offered by providers such as Amazon Web Services (AWS KMS), Google Cloud KMS, and Microsoft Azure Key Vault manage encryption keys and encrypt data at rest or in transit. Without special hardware, these providers, like is*hosting, ensure data security through automatic key rotation, management, and access control.
With the scalability of clouds and compliance with security standards such as GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and PCI-DSS (Payment Card Industry Data Security Standard), cloud encryption services allow organizations to maintain the encryption of data stored in the clouds. These methods provide reliable protection while simplifying encryption management.
5 Best Practices for Implementing Data Encryption

The following list presents five best practices for implementing encryption methods in various use cases and strengthening your data security posture.
- Choosing the suitable encryption method
Choosing the correct encryption method depends on the sensitivity of the data, the performance requirements, and the use case. For large data sets, symmetric encryption (such as AES) is preferred for its speed, while asymmetric encryption (such as RSA) is ideal for secure key exchange and authentication. However, a combination of both methods is often recommended.
- Key management strategies
Successful encryption requires effective key management. This includes secure storage, distribution, and rotation of data encryption keys. Hardware security modules (HSMs), key management services, or cloud-based key management solutions are good options in this case. It’s also important to rotate and revoke keys regularly to reduce vulnerabilities and ensure proper access controls.
- End-to-end data encryption
End-to-end encryption ensures that data remains encrypted during transit and at rest, protecting it from unauthorized access at every process stage. Since only the intended recipient can decrypt the data, this enhances security. This method is critical for sensitive communications, such as messaging apps, as it prevents interception in transit or at rest.
- Compliance and regulatory requirements
Organizations must implement encryption methods that comply with regulatory requirements such as GDPR, HIPAA, and PCI-DSS to avoid fines and protect sensitive information. Regular audits and compliance checks are also necessary to help maintain compliance with these standards.
- Data encryption performance and scalability
Successful encryption implementation depends on balancing security and performance. While symmetric encryption is faster for large amounts of data, hybrid encryption methods optimize performance during key exchange. To ensure that encryption processes scale according to the organization's needs, it is necessary to use scalable cloud encryption solutions, optimize algorithms, and regularly monitor system performance.
These encryption best practices are important to protect sensitive data in various industries. The following section will discuss the most common use cases for encryption.
Data Encryption Challenges

While data encryption is necessary to protect sensitive information, it often presents several challenges for organizations to overcome. Organizations must be able to manage these challenges to remain operational and compliant. The following outlines the main encryption challenges and tips on how to avoid them.
Performance Impact
One of the biggest concerns is the potential impact of data encryption on system performance. Encryption processes can slow data transfers and increase resource consumption when dealing with large data sets or real-time applications. Although symmetric encryption is faster, it requires careful optimization to minimize overhead, while asymmetric encryption can be slower due to the complex key generation and exchange processes.
Tip: In such cases, a balance of security and performance can be achieved through efficient modern encryption algorithms and hardware resources to maintain smooth operation.
Complexity of Key Management
Proper data encryption key management is essential to maintaining data security encryption, but it can be very complex. Key management involves the secure creation, storage, distribution, rotation, and revocation of encryption keys. Any action performed incorrectly can lead to security vulnerabilities or data leaks. For large organizations, managing multiple keys across different systems and applications increases the risk of human error.
Tip: When key management is a challenge, critical management services and hardware security modules (HSMs) can help, but they also add additional cost and complexity to your infrastructure.
We've got your back with reliable storage for backups of your projects. is*hosting solutions are your go-to for data protection.
Data Encryption and Regulatory Compliance
Ensuring encryption is compliant with regulatory standards can pose another challenge. As mentioned earlier, organizations must implement encryption methods that comply with regulatory requirements such as GDPR, HIPAA, and PCI-DSS to protect sensitive data. Failure to comply can result in significant fines and legal consequences.
Tip: Encryption must be carefully implemented to balance compliance with operational needs. Some regulations require detailed audits and frequent updates to encryption methods, which increases the administrative burden.
Decrypting Encrypted Data in Security Breaches
Decrypting compromised data can be a significant challenge in a security breach. If encryption keys are not correctly protected, attackers can access encrypted data, rendering encryption useless. Additionally, companies may sometimes need to decrypt large amounts of data quickly for investigation or remediation.
Tip: To efficiently handle the decryption of encrypted data without compromising its integrity or security, it is necessary to implement robust critical protection and recovery mechanisms.
Real-World Examples of Data Encryption

Encryption is vital across various industries to ensure compliance and protect sensitive data. In the following sections, you can learn about real-world examples of encryption that highlight its importance and impact across different industries and services.
Data Encryption in Financial Services
Financial services remain a prime target for cyberattacks, with 63% of financial institutions reporting increased cyber threats in recent years. Encryption protects personal data such as customer account information, credit card numbers, and transaction records. Most of this data is encrypted with AES at rest and in transit. For example, JPMorgan Chase uses end-to-end encryption to protect more than 50 million transactions made daily. The PCI-DSS standard requires strong encryption for payment processing, ensuring that sensitive financial data remains secure.
Data Encryption in Healthcare
Healthcare data breaches are becoming increasingly common; more than 29.3 million medical records were exposed in 2020 alone. Encryption plays a significant role in HIPAA (Health Insurance Portability and Accountability Act) compliance, requiring patient data encryption at rest and in transit. Cleveland Clinic and other considerable health systems use AES-256 encryption to secure electronic health records (EHRs), ensuring the security of over 7 million patient records. As of 2024, AES-256 encryption remains the most widely used standard, protecting millions of EHRs across large healthcare organizations. Strong encryption reduces the risk of unauthorized access during cyberattacks, mitigating potential breaches and enhancing patient privacy.
E-Commerce and Payment Security
The e-commerce industry processes billions of transactions yearly, making it a prime target for cybercriminals. In 2020, e-commerce fraud resulted in $17.5 billion in losses worldwide. Encryption is critical to protecting payment data and customer information. TLS/SSL encryption protects payment transactions by encrypting data between customers and e-commerce platforms. Large companies like Amazon and Shopify use TLS encryption to protect the data of millions of users. The PCI-DSS compliance standard requires encryption of payment information, ensuring the security of credit card data and personal information.
Virtual private servers - optimal hosting for websites. Fast NVMe drives, over 30 countries, always scalable.
Government and Military Data Encryption Standards
Government and military agencies handle sensitive information that could pose a security risk if compromised. United States federal agencies use FIPS 140-2 encryption to protect sensitive data. The National Security Agency (NSA) uses AES-256 and ECC to protect classified communications. Military encryption systems are designed to protect data in the field, ensuring secure communications and data protection for millions of active duty personnel and defense infrastructure.
These real-world use cases demonstrate how encryption is essential across industries. It provides important protection for sensitive data and helps organizations meet regulatory requirements.
Conclusion
With the rise of increasingly sophisticated cyber threats today, data encryption is vital to protect sensitive information across industries. Encryption methods also need to evolve to remain reliable and effective. Future data encryption trends include post-quantum cryptography, designed to protect against quantum computing threats, and developing standards such as AES-256 and ECC, which will remain critical to data protection. Homomorphic encryption and zero-knowledge proofs offer new ways to enhance privacy while maintaining data security. Organizations must keep up with these advancements and ensure their encryption methods remain robust in an increasingly complex digital landscape.
Dedicated Server
You get smooth operation, high performance, and easy-to-use setup, providing a complete solution for your needs.
From $70.00/mo