In today's Internet world, we spend a lot of time online. At home or at work, we buy more and more Internet of Things (IoT) devices with wireless connections for convenience. Since these devices are most often connected to a single Internet access point, we need to make sure that the security of the Wi-Fi network, and therefore the security of our data, is up to par. That's why Wi-Fi network security is becoming increasingly popular.
In this article, we will discuss why network security is important, how to protect your home, small business, and enterprise wireless networks, and how to identify and respond to security threats and attacks.
Having gained access to your local network, a cybercriminal can easily gain access to your personal data and launch various attacks, including outright data theft. That's why protecting your network from cyberattacks is more essential than ever. To protect your devices from hackers and cybercriminals, it's necessary to understand and know how to secure your home Wi-Fi networks, and you don't have to be a tech expert to do it.
Tips for Setting up a Secure Home Wi-Fi Network
We have selected the top 5 tips for setting up a secure home Wi-Fi network that will help reduce the risk of someone hacking your Wi-Fi-enabled devices and personal data.
Use a Strong Network Password
Creating a strong network password is one of the most important rules for maintaining a secure connection. Preferably, use a password that is at least 12 characters long, including a combination of uppercase and lowercase letters, numbers, and special characters. Do not use passwords or words that are easy to remember, such as names, birthdates, phone numbers, and other common data. Simple Wi-Fi passwords are easy to remember and decipher. The most essential thing is to try to update your Wi-Fi password regularly to improve security.
Enable WPA2 or WPA3 Encryption
When connecting to a Wi-Fi network at home, it is also worth checking your router. New routers must support WPA3, while less-than-modern devices rented from a provider use WPA2. Then, to improve security, it comes to upgrading routers to WPA3. To learn more about enabling WPA2 or WPA3 encryption to secure your Wi-Fi network, check out our article on “WEP, WPA, WPA2 and What Comes After: An Overview of Wireless Security Protocols”.
Hide Your Wireless Network Name
The easiest way to secure your home Internet connection is to change your settings, SSID, and password. SSID (Service Set Identifier) is a wireless network identifier. SSID is the default (factory) name of the Wi-Fi network that is displayed on your computer, phone, and other devices. The factory SSID is also indicated on the router itself. To change the SSID and password, follow these steps:
- To open the command line, simultaneously press the Windows + R keys on your keyboard.
- In the field, enter cmd and click OK.
- In the new window that opens, type ipconfig.
- Press Enter.
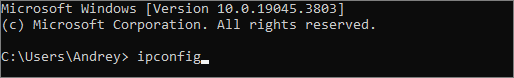
- Find and copy your IP address in the “000.000.0.0” format.
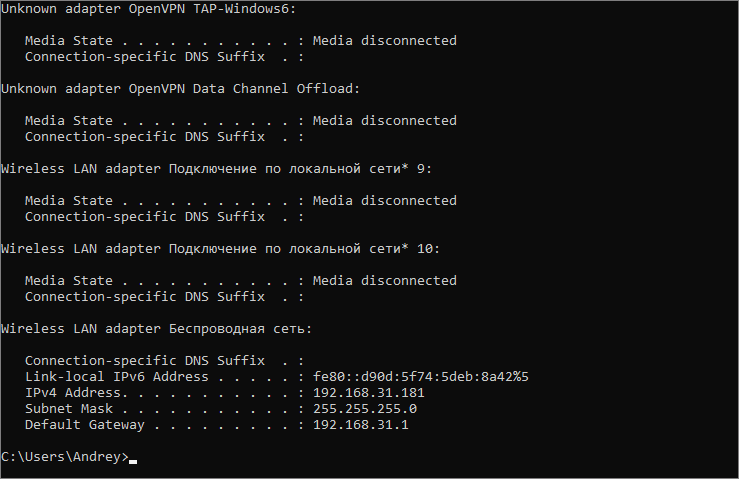
- Enter your router login credentials.
- Change the SSID and password in Wi-Fi settings.
When changing the SSID and Wi-Fi password, do not use obvious personal information, try to incorporate longer words and sets of numbers.
Use MAC Address Filtering
All devices on the network have a media access control (MAC) address. By filtering MAC addresses, you can allow access to only authorized users.
To determine the MAC address and configure filters, follow these steps:
- Open the command line using the method you know best.
- In the new window that opens, enter ipconfig/all.
- Press Enter.
- In the Wireless LAN Adapter section, the Physical Address line will display the MAC address of the wireless adapter.
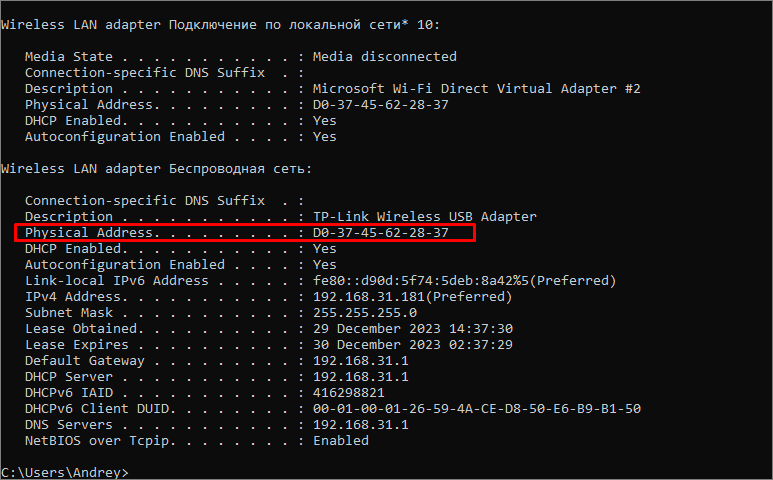
- Find and copy your IP address in the format “000.000.0.0” into your browser.
- Enter your router login credentials.
- Go to the MAC filter subsection in the Wi-Fi section, where you can change the modes: Disabled, Allow, Deny.
- If you want to allow all connected devices to access your wireless network, use the Disabled mode.
- If you want to allow access to devices whose MAC addresses are added in the MAC addresses section, use the Allow mode.
- If you want to deny access to devices whose MAC addresses are added in the MAC addresses section, use the Deny mode.
You can also use a "guest" account, which allows guests to use your wireless channel with a unique password, keeping your important credentials private.
Update Router Firmware
Your router's firmware is critical to ensuring a secure network connection. You will have to manually update the software on most wireless routers that are not automatically updated. Each router manufacturer has its own process for updating software. By visiting the manufacturer's website, you'll be sure to find instructions on how to download the firmware update file, as well as how to install it directly onto your wireless router.
Enable Firewalls
Most wireless routers are already equipped with excellent hardware firewall features. An effective firewall prevents unauthorized traffic on your wireless network without your awareness. In order to enable router firewalls, which are often not enabled by default, you will also need to log in using your IP address to your router's settings, where you can control this feature: activate router firewalls to prevent unwanted traffic or disable them to improve your Internet access speed.
Monitor Your Home Network Activity
The protection and privacy of your devices connected to your home network depends on the quality of setting up a secure home Wi-Fi network. You can learn more about how to manage your Wi-Fi network, namely how to check the browsing history on your Wi-Fi router and monitor the activity of your home network in our article "How to Check Browsing History on a Wi-Fi Router".
Securing Small Business and Enterprise Networks
Using a Dedicated Server or VPS
It is especially important for small business and enterprise owners to take steps to block unauthorized access attempts and protect the confidentiality of company information and data. Here, companies often resort to using VPS and dedicated servers that offer exclusive resources. VPS and dedicated servers are some of the most attractive hosting options in terms of the price-quality ratio. VPS scales resources and provides secure hosting, while dedicated servers provide consistently high performance and maximum security for confidential data. When ordering VPS, you can choose hosting with or without a control panel. We offer clients the following panels: ISP Manager, DirectAdmin, VestaCP, HesticaCp, aaPanel, FastPanel, and their variations.
VPN and Encryption Protocols
A VPN connection and the encryption protocols used in VPN technology help protect transmitted data. VPN is a virtual private network, a kind of tunnel between devices that protects transmitted data through encryption protocols. The protocols encrypt various data by changing IP addresses and locations in such a way that no third party can obtain your data.
Antivirus and Anti-Malware Tools
Antivirus software not only detects malware threats, but also prevents and removes viruses. Modern antiviruses are able to analyze the actions or intentions of malicious files and determine suspicious content by using predictive analytics based on machine learning and artificial intelligence. You can learn more about the types of paid and free antiviruses in our article “Free and Paid Antivirus Protection: Best Solutions Review”.
Monitoring Network Traffic
To protect small business and enterprise networks, an important task when building a network is the well-planned interaction of devices, the ability to manage connected devices and monitor network traffic. In our article “How to Check Browsing History on a Wi-Fi Router” you can find a lot of useful information about tools and methods for monitoring network traffic.
Responding to Security Threats and Attacks

Incident Response is a whole set of activities and stages that include identifying and stopping a cyberattack or data leak from an organization’s infrastructure and eliminating the consequences. The main goal of responding to security threats and attacks is to minimize the incident's damage and allow the enterprise to return to normal systems operation as quickly and cost-effectively as possible.
Incident response begins with identifying suspicious activity. When a cyberattack is notified, experts assess the threat and collect data about it. Thus, the stage of assessing the severity of the attack begins, after which measures are promptly taken to stop the spread and eliminate the threat. For example, hacked devices are disabled, passwords and credentials are changed, lost data is restored, etc.
At all stages of incident response, it is necessary to contact the appropriate IT security experts, who will not only help to identify, assess, eliminate threats, and bring the system back into operation in the shortest possible time but also propose a plan to improve the response to security threats and attacks, taking into account experience gained in eliminating a cyberattack.
Conclusion
As information technology evolves, new types of cyberattacks are emerging in parallel. Therefore, it is critical to be able to protect both home Wi-Fi networks and small business and enterprise networks from the threat of these attacks. It is also essential to be able to respond quickly to incidents to minimize damage and promptly normalize system operation. We hope that our article will prove useful to you in setting up a secure Wi-Fi network, and that our services, which you can order on the website ishosting.com, will help to effectively protect your transmitted data from unwanted leaks and third parties.
VPS
Choose the suitable configuration and enjoy all the benefits of a virtual private server.
From $4.99/moPersonal VPN
Stay anonymous online with a dedicated IP and don't endanger your personal data.
Get $5.00/mo