It's no secret that it is difficult to keep up with rapidly developing technologies in today's virtual world. However, it is very important to keep up with them and know how to respond promptly to emerging advanced threats, especially for your personal or corporate security. How can you secure your and your company’s network, work remotely, and have access to securely encrypted internal company resources such as files, apps, and databases?
Today, we will learn about such an additional and reliable method of network security as L2TP/IPsec. What is it, and how does it work? Why do you need this, and how to configure it on different OSes? We will talk about all this in our article.
What is L2TP/IPsec?
L2TP/IPsec are two protocols that perfectly complement each other with their functionality.
L2TP (Layer 2 Tunneling Protocol) is a protocol that is used in virtual private networks, supports them, and allows you to create a tunnel for additional security.
IPsec (Internet Protocol security) is a highly adaptive end-to-end security protocol that authenticates and encrypts every IP packet contained in a given message. Many apps use IPsec at the network layer of the TCP/IP protocol stack.
Although L2TP and IPsec are two full-fledged protocols with certain characteristics, they are more often used together. Where L2TP is blocked by firewalls, IPsec comes to the rescue. Combining their functionality in use and creating a secure communication channel between remote employees and the corporate network, L2TP and IPsec are excellent for security and anonymization.
Another protocol combination you might be interested in is Shadowsocks with OpenVPN.
How It Works
The principle of L2TP and IPsec protocols is to create a virtual private network connection between a client and a server. This is done using attack detection and prevention mechanisms, data encryption, and authentication.
The L2TP protocol allows data to be transferred over multiple protocols, such as IP, IPX, or NetBEUI, without changing the current network settings. In addition, L2TP allows data to be routed across different networks, providing flexibility and efficiency in data transfer.
In corporate networks where a secure connection between remote offices is required, L2TP/IPsec is used. Virtual private networks (VPNs) also often use protocols to allow users to communicate securely over public networks such as the Internet.
L2TP/IPsec Usage
L2TP/IPsec is widely used in networks for data protection and security. Its primary use is to create virtual private networks (VPNs) and the following applications:
- Convenient, secure remote access to a business network.
- Securing Wi-Fi with additional encryption and authorization.
- Protecting VoIP traffic with a secure and encrypted connection, ensuring uninterrupted and confidential communication between participants.
- Ensuring secure connection between two or more networks.
Is L2TP/IPsec Better than OpenVPN?
Today, the market offers several protocol options for implementing a virtual private network. OpenVPN remains the most popular so far, being a free and open-source solution. L2TP/C, like OpenVPN, is available on all modern operating systems: Windows, macOS, Linux, Android, iOS. However, it is interesting how L2TP/C and OpenVPN differ. We offer a comparison table with the obvious differences between these two protocols:
|
L2TP/IPsec |
OpenVPN |
|
|
It's up to you to decide which protocol is important for you and your security. We will then proceed to configuring L2TP/IPsec on different OSs and tell you how to do it.
Configuring L2TP/IPsec on iOS
To configure L2TP/IPsec on any OS, you need to get configuration files. After renting a VPN server and activating the service, you can download configuration files to your device and receive access information via email or find them in your hosting provider’s personal account. Now we will show how to find access information in your personal account. To do this, follow the steps:
- Go to the VPN Servers tab in your personal account.
- Click Manage.
- In the Access section, find the PPTP/L2TP settings.
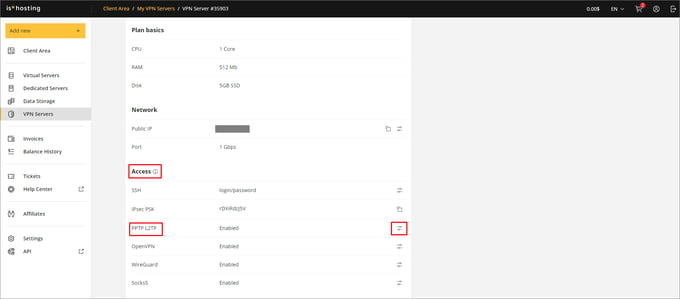
- Download access information there.
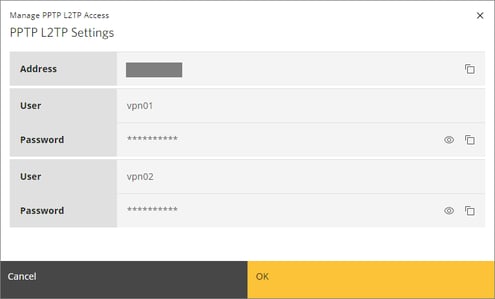
Now we’ll tell you about configuring L2TP/IPsec on iOS.
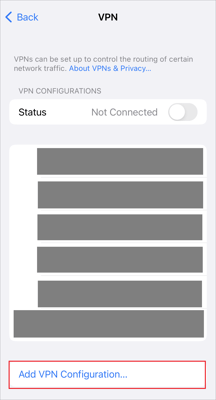
In order to configure VPN connections via L2TP on your iPhone/iPad, you need to enter data for certain parameters in the VPN section on your devices. You can find this section by going to Settings > General.
Next, follow the steps:
- Go to VPN & Device Management.
- Open the VPN section.
- To add a VPN configuration, click the Add VPN Configuration button.
- To configure the VPN connection, enter the following parameters :
Connection Type – L2TP.
Description – any of your choice, for example, "is*hosting".
Server – IP address of the VPN server.
Account – PPTP/L2TP username.
Password – PPTP/L2TP password.
Shared key (Secret) – ipsec shared PSK.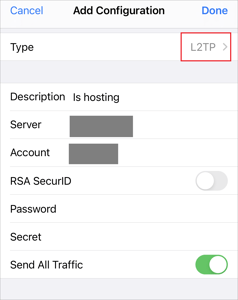
- Write the access information from the message you received by email when the service is activated.
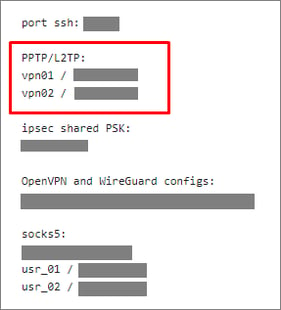
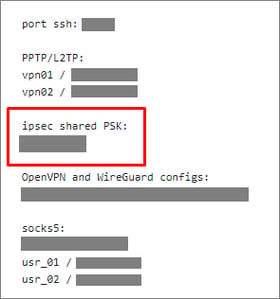
- Also, as mentioned at the beginning of the section, you can find the access information to L2TP/IPsec in your hosting provider's personal account.
- After entering all the data, click Done.
- Slide the switch to the right to connect to the added VPN configuration.
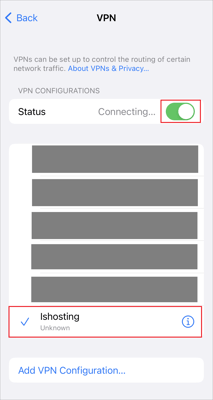
If the connection is successful, you see the Connected status.
Setting up L2TP/IPsec on Android

To install and configure VPN L2TP/IPsec connection on your Android device, you also need to go to the Settings menu of your device and follow the steps:
- In the Wireless Networks section, select More or Another Settings.
- Go to the VPN menu item.
- Click the + or other relevant button to add a new VPN connection.
- Select the L2TP/IPsec PSK connection type on the next screen and enter the required VPN connection parameters. You can also find all configuration files and access information in the message that you received by email when activating the service or in your personal account of your hosting provider in the VPN servers tab.
- Click Save to save the created VPN connection.
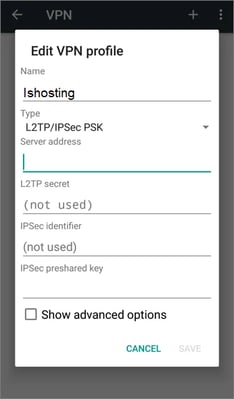
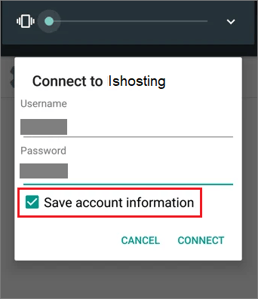
- If you do not want to enter data for reconnection, click the name of the created VPN connection, enter your username and password, and check Save account information.
- Check the Always VPN checkbox only to allow traffic when connected to this VPN.
- Click Connect.
L2TP/IPsec Configuring on Windows

Installing and configuring VPN L2TP/IPsec Connection on your Windows OS (versions 7, 8.1, 10, 11, 2008R2, 2012R2, 2016, 2019, 2022) is just as easy. In the Start menu select Settings and find Network & Internet there.
Next, follow the steps:
- Click VPN in the Network & Internet menu bar on the left and select Add a VPN connection.
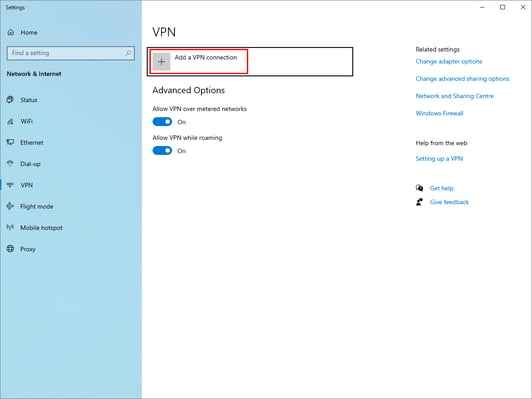
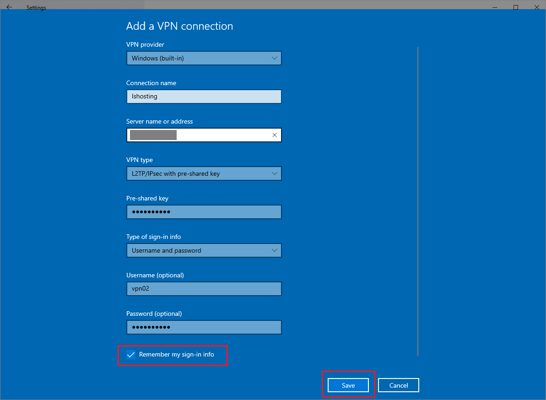
- Specify all the necessary parameters and access data from the configuration files that you received by email in the message after activating the service. Let us reiterate that you can also find access information in your personal account of your hosting provider in the VPN servers tab.
- If you do not want to reenter the password each time you connect, select the Remember my sign-in info checkbox and click Save.
If the connection is successful, the Connected status appears and you can track VPN usage statistics.
Configuring L2TP/IPsec on macOS
To configure the L2TP/IPsec connection on your macOS, go to the System Settings… and follow the steps:
- Go to the Network section.
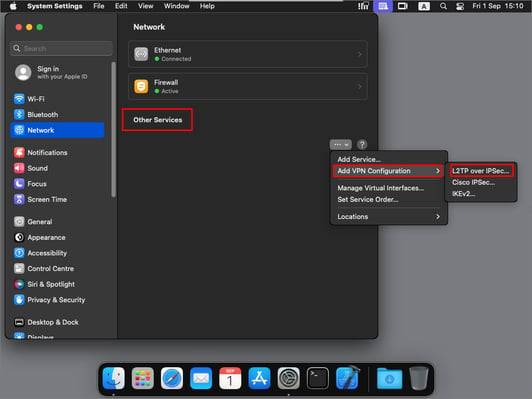
- To add a new VPN connection, go to the Other Services field.
- Click Add VPN Configuration > L2TP over IPSec….
- In the opened window, enter the VPN connection parameters and click Create.
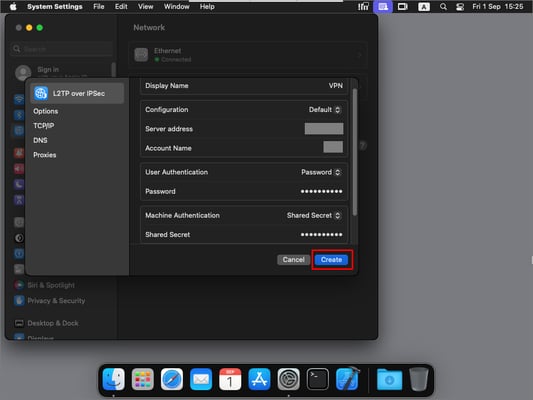
- Enter the parameter data from the message you received by email when activating the service or from your hosting provider's personal account.
- VPN connection successfully configured.
- To connect, slide the switch to the right.
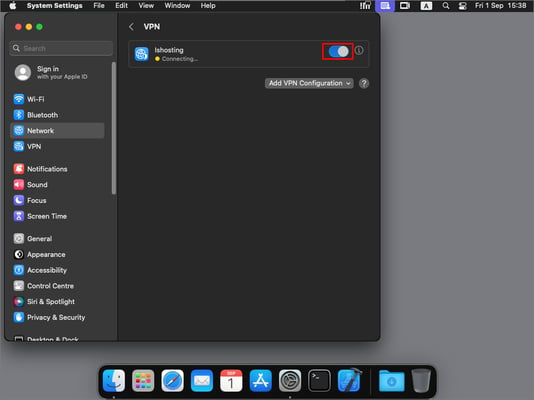
If the connection is successful, the Connected status will appear, and you can track your VPN usage statistics.
Conclusion
In conclusion, we will summarize and list the main points of using L2TP/IPsec, touching on the advantages and disadvantages of this protocol.
- L2TP/IPsec is included in all modern operating systems and VPN devices.
- Configuring L2TP/IPsec is intuitive and straightforward.
- The combined operation of these two full-fledged protocols ensures strong encryption, security, and confidentiality of traffic passing through them.
- L2TP/IPsec works slower than others because of the 3rd step.
- Since L2TP uses UDP port 500, a firewall may block it if you are behind a NAT, but IPsec is currently considered highly secure to use and does not contain any severe vulnerabilities
Personal VPN
VPN for those who want to remain undetected online and secure their data. Dedicated IP and complete anonymity.
VPS
Choose the suitable configuration and enjoy all the benefits of a virtual private server for VPN.
From $5.00/mo