Imagine that an employee's job involves using a particular set of programs - engineering, accounting, design, and so on. Suddenly the workstation becomes unavailable. For example, the specialist is sent on a business trip or for a refresher course.
In such a situation, it is quite possible to continue some or all of your work simply by having a laptop or tablet with Internet access at hand. However, it is not always possible to install working programs on portable devices. This is where Microsoft's RDP protocol comes in.
What is RDP in computer?
Remote Desktop Protocol (RDP) is a technology designed to easily connect to Windows-based computers and servers. RDP allows users to remotely connect to other computers and access their features.
RDP uses various encryption and security mechanisms to protect data transmitted between the client and the remote computer, ensuring confidentiality and integrity. RDP can be used for tasks such as remote administration, technical support, or accessing files and applications on a remote system.
How does remote desktop protocol work?
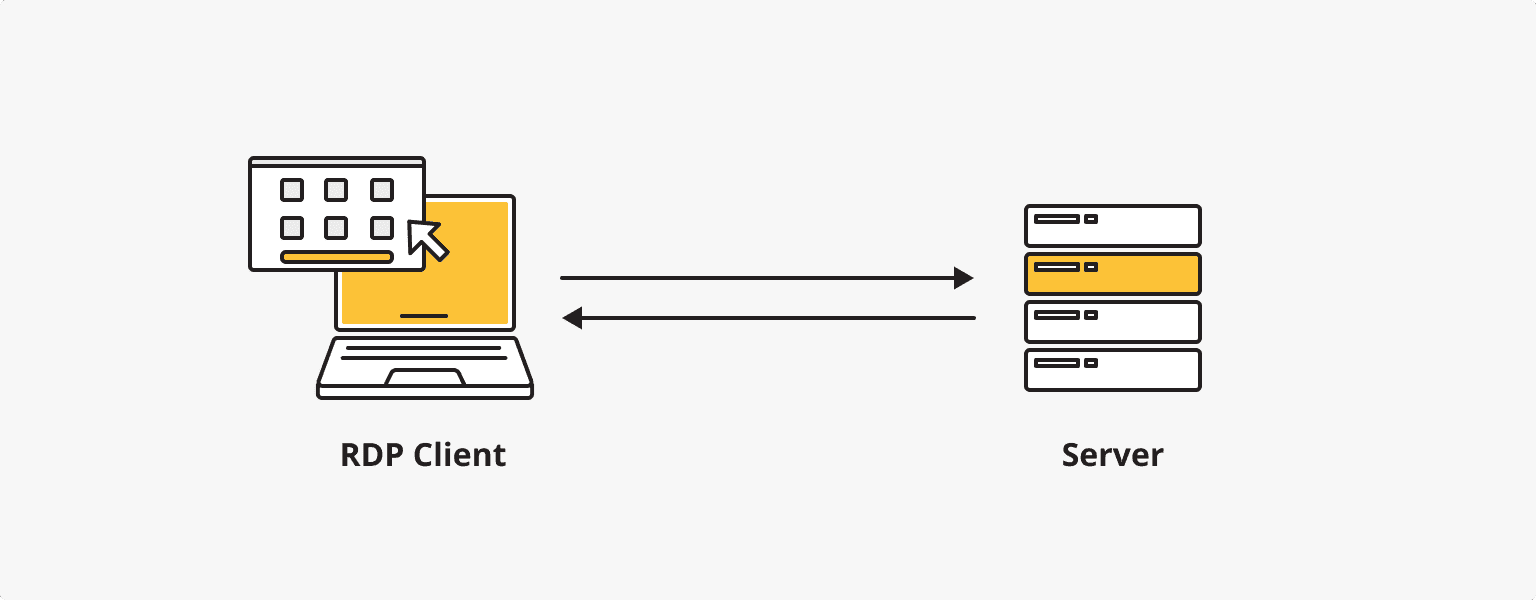
The Remote Desktop Protocol works by establishing a connection between a user's computer (RDP client) and a remote server or computer, allowing the client to access and control the remote computer's desktop.
The client computer initiates an RDP session by sending a request to connect to the remote server. The client and server 'negotiate' the security details for the new session. Is rdp traffic encrypted? Yes, this includes encryption methods, authentication protocols, and other necessary parameters.
The remote server verifies the credentials provided by the client to ensure authorized access. This step typically involves username and password verification or other forms of authentication such as smart cards or biometrics. Once authenticated, the server creates a new user session for the client. This session represents the remote desktop environment that the client will have access to.
A remote server using RDP displays the full desktop environment, including applications, graphics, windows, icons, and other common visual elements. Special graphics optimization reduces latency and bandwidth requirements.
The client computer records the user's input, including keyboard and mouse actions. It sends this data over the network to the remote computer. And to minimize the amount of data transferred between the client and the remote server, only the parts of the screen that change are transferred.
When an RDP session is terminated, either by disconnecting the user or by explicitly terminating the session, the client and remote server clear the session resources and end the connection.
What's RDP used for: Remote Desktop use cases
Remote Desktop is a versatile technology that can be used in a variety of situations. Some common uses of RDP include:
- IT administrators can use Remote Desktop to troubleshoot remote computers or servers and perform other maintenance tasks without being physically there.
- Remote Desktop allows employees to work from home or any other location while still having secure access to their office computers. This includes teamwork and sharing the resources of a remote server or computer.
- RDP is widely used by technical support departments to help users. Technical support specialists can connect to a user's server, view the desktop and resolve issues directly.
- Developers often use Remote Desktop Protocol to access remote environments for software development, testing, and debugging.
Advantages of RDP
- Hardware independence.
- Work from anywhere in the world.
- High-speed data transmission.
- Multi-user mode support.
- Easy to learn end-user client software.
RDP makes it possible to operate the most powerful computing systems from an ordinary laptop. The protocol works fast, even on laptops with limited hardware resources. The only limitation is the Internet bandwidth: a minimum speed of 256 kbps is required.
Is RDP secure? RDP vulnerabilities
During the coronavirus pandemic, the number of RDP attacks rose sharply, according to Eset. The quarantine forced organizations to adopt previously under-utilized technologies, including Microsoft's protocol. How to secure your RDP experience will depend on your skills, the organization's overall security policy, and the activities of hackers. It is, therefore wise to be aware of the most common hacking techniques used by cybercriminals.
Password brute-forcing
A method by which a hacker attempts to gain access to a system by brute-forcing passwords. The number of attempts is often in the millions. These are carried out using special applications written by the criminals themselves or by less scrupulous programmers. So, hackers know how to hack rdp username and password.
Once connected, fraudsters use a variety of methods to steal confidential information and infect systems. Ransomware is particularly common on computers - viruses that encrypt important files and then demand payment in cryptocurrency to unlock them. Brute forcing of passwords is an old but effective strategy. Users often choose combinations like "qwerty" or "123456" for their passwords, forgetting about security. To avoid making life easier for criminals, experts recommend using more complex combinations of random characters, such as "-aif%h+-9sudgfa9suid()fh". How to make a strong password?
Stealing of credentials
This type of attack is aimed at obtaining data to gain access to some systems. And often, it is not necessary to resort to social engineering or devise multi-pronged operations to deceive victims in order to obtain this data. Accounts are constantly being leaked onto the World Wide Web through the carelessness of users and system administrators.
As with password brute forcing, attackers do not manually monitor data leaks; the process is performed by special programs. Special bots (a type of computer virus) are used to bypass firewalls. And because the accesses come from different IP addresses, firewalls do not raise any alarms.
Sometimes, due to the carelessness of system administrators, a single password can give access to many accounts. A competent administrator must ensure that no login combinations are repeated within a single system. If knowing all the logins, a single account is successfully compromised, it is easy to check the others.
Password spraying attack
A method by which a hacker guesses username/password combinations and attempts to log into multiple accounts. Criminals obtain background information for hacking in a variety of ways, such as by tracing information from public sources.
Once a victim has been identified, the attacker uses LinkedIn, for example, to find out about the specialists on the website of the organization he is going to attack. And to find out the password and lockout policy rules of Active Directory (directory service), it is not necessary to hack into hundreds of accounts, just one. The same ransomware is then installed, or the passwords continue to be distributed within the domain.
How to secure RDP

By taking a few precautions, you can protect yourself from hacking when using RDP:
- Keep the number of Internet connections to a minimum.
- Password-protect your security features to prevent possible deletion.
- Set up an additional authentication mechanism.
- Set unique and strong passwords for all accounts.
- Disable external connections to local computers on the RDP port.
- Use a VPN.
- Disconnect machines running older operating systems from the WAN.
The most important thing to remember is that you should never use RDP over an open Internet connection! If you need to communicate with your computer online, always encrypt the traffic.
Secure Alternatives to RDP
Microsoft provides a built-in remote desktop feature in Windows operating systems. This allows you to connect to other Windows machines remotely.
However, several third-party remote desktop programs, such as TeamViewer, AnyDesk, and VNC, offer cross-platform compatibility and additional features beyond RDP's built-in capabilities.
VNC is a platform-independent remote desktop protocol that allows users to access and control remote computers. VNC is available in several implementations, including RealVNC, TightVNC, and UltraVNC.
TeamViewer is also a widely used remote access and support software that allows users to connect to remote computers, transfer files, collaborate, and provide necessary technical support. It provides cross-platform support and works through firewalls and NAT without requiring complex network configuration.
AnyDesk, as an alternative remote desktop software, provides high-quality graphical transmission and supports features such as file transfer, session recording, and remote printing. AnyDesk is known for its low latency and efficient use of bandwidth.
Other alternatives include Chrome Remote Desktop, LogMeIn, Splashtop, etc.
Should VPNs replace RDP?
VPN (virtual private network) and RDP serve different purposes, although they can be used together. Some argue that VPN and RDP are functionally similar in that they allow you to connect to a remote 'point' without being physically present, but these two terms are not related. A VPN cannot replace the functionality of RDP.
A VPN creates a secure and encrypted connection between your device and a remote server, ensuring the privacy and security of your data as it passes through a special tunnel. RDP is a protocol designed specifically for remote access and desktop management.
A VPN can enhance the security of an RDP connection by encrypting the traffic between the client and the RDP server. A VPN provides secure access at the network level, while RDP provides secure access at the desktop level.
You could use a VPN based on your corporate network or your own VPN on the VPS to make sure you have a secure connection. It would be a mistake to choose a shared VPN service! The most secure option is an in-house VPN based on a virtual private server. is*hosting offers 25 locations where you can choose a VPS and a suitable static IP address for your personal VPN.
Personal VPN
For those who want to remain undetected online and secure their data. Dedicated IP and complete anonymity.
24/7 Support
Rely on us. is*hosting technical support is available 24/7 and does not ignore customers.
More