Wireless networks were first developed in the 1990s using spread spectrum technology, which spread the data signal over a wide range of frequencies, making it difficult for unauthorized users to intercept data.
In the early 2000s, Wi-Fi was introduced, based on the IEEE 802.11 standard, making new networks faster and more secure than spread spectrum networks.
Currently, there are various Wi-Fi standards, such as 802.11a, 802.11b, 802.11g, 802.11n, and 802.11ac, each with distinct speed and security features
Wireless Network Security
Wireless networks have been popular for a long time because they offer a convenient way to connect to the internet without cables. However, they are more vulnerable to security breaches than wired networks because anyone within range can access them.
The Wi-Fi Alliance, a non-profit organization that owns the Wi-Fi trademark, certifies all Wi-Fi security protocols. The most common protocols are:
- WEP, one of the oldest wireless security protocols, is not very secure and can be easily hacked.
- In contrast, WPA is a more secure protocol that uses an improved encryption algorithm and is more challenging to crack.
- Currently, WPA2 is the strongest wireless security protocol available.
Wi-Fi security protocols utilize cryptographic keys to randomize data, making it indecipherable. Since Wi-Fi systems use symmetric encryption, the same key is used for encrypting and decrypting data.
What is WEP (Wired Equivalent Privacy)?
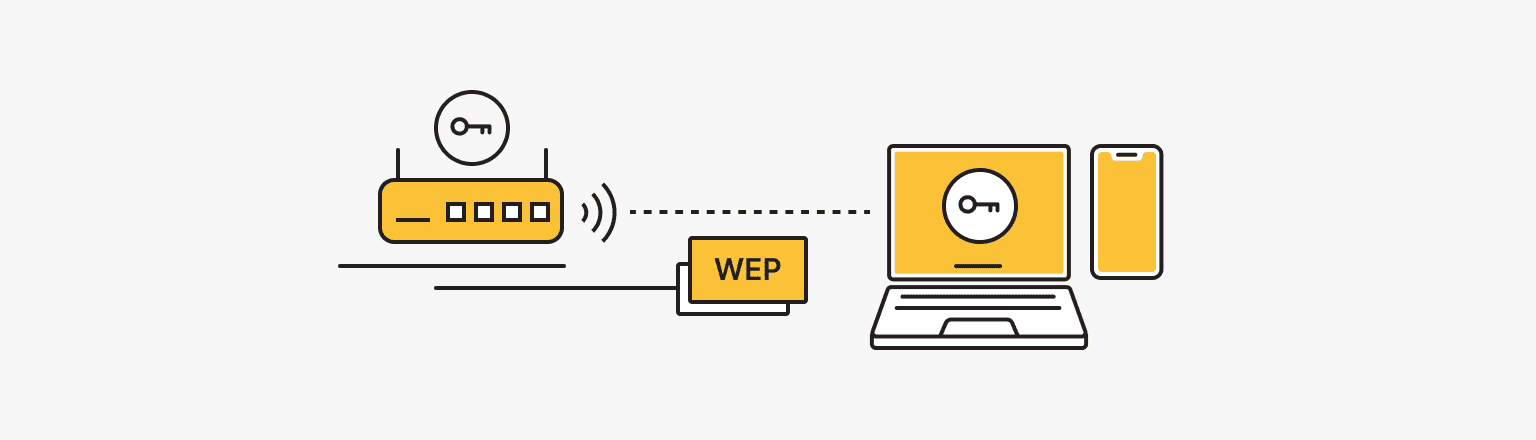
WEP (Wired Equivalent Privacy) was developed in the late 1990s to secure wireless networks, which were becoming popular but lacked security. It aimed to provide a level of security equivalent to wired networks.
WEP is an encryption protocol based on the RC4 algorithm. Although RC4 was considered a robust encryption algorithm at the time, it is now known to have vulnerabilities that make it easy for attackers to break. It was standardized in 1999 by the IEEE as part of the 802.11b standard, which was the first widely adopted Wi-Fi standard. Despite being the default security protocol for 802.11b networks, WEP is no longer recommended for use due to its weaknesses.
Wireless devices encrypt data with a key before transmitting it over the network. The access point then decrypts the data using the same key.
Originally, WEP used a 64-bit key with the RC4 stream encryption algorithm to encrypt data transmitted over a wireless network. Later versions of the protocol added support for 128- and 256-bit keys to increase security. To achieve this, WEP uses a 24-bit initialization vector, resulting in effective key lengths of 40, 104, and 232 bits.
WEP has several vulnerabilities. One of them is that all devices connected to the wireless network share the same encryption key, which does not change over time. Additionally, WEP has a limited capacity for encrypting data, only supporting up to 1500 bytes. This limitation puts larger data packets, such as video and audio files, at risk.
Transition to WPA (Wi-Fi Protected Access)
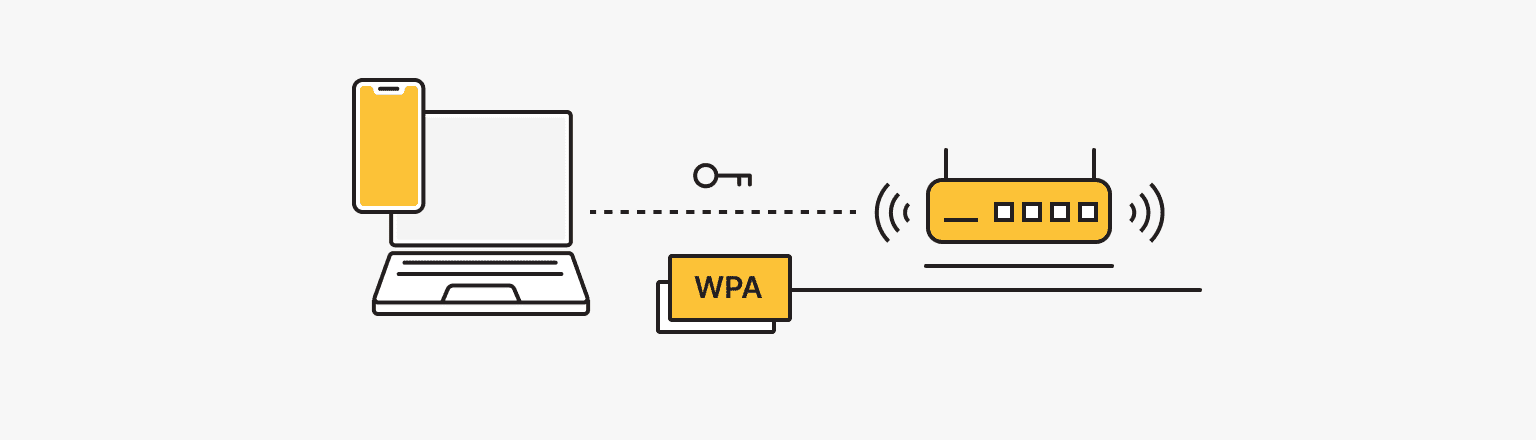
WEP was quickly recognized as insecure and was replaced by WPA (Wi-Fi Protected Access) in 2003. WPA is more secure than WEP, utilizing stronger encryption algorithms, stronger authentication protocols, and broader security features. Additionally, WPA has introduced new security features.
- New encryption algorithm TKIP (Temporal Key Integrity Protocol).
- MIC (Message Integrity Check) data validation tool.
- New authentication protocol with a wider range of methods EAP (Extensible Authentication Protocol).
WPA supported various security methods, such as PSK (Pre-Shared Key), 802.1X, and RADIUS.
The WPA system utilizes a centralized architecture with a single authentication server responsible for handling all requests. This makes it more difficult for attackers to gain access to the network, as they would need to compromise the authentication server to do so.
However, WPA has yet to become the standard for security. WPA uses a pre-shared key that all devices on the network are aware of. This key can sometimes be guessed or compromised, putting the entire network at risk. The temporary key used to encrypt data can sometimes be detected by intercepting initialization vectors transmitted in the clear, which allows traffic to be decrypted. In WPA, certain management frames are not encrypted, which can lead to connection breaches.
The 'WPA None' parameter in WPA allows for unencrypted traffic, which defeats the protocol's purpose and requires proper configuration.
WPA2: Improvements and Enhancements
WPA2, introduced in 2004 as the successor to WPA, is currently the most widely used WiFi security standard. Its purpose is to address the weaknesses of WEP encryption and enhance the security of device authentication and traffic encryption.
The technical features of WPA2 are:
- The AES encryption algorithm is used for strong symmetric traffic encryption.
- The technology supports 802.1X/EAP protocols for device authentication using an internal authentication server.
- Random PMK and PTK keys are generated per session for encryption instead of a shared key.
- Key transfer protocols, such as the 4-way handshake, are implemented to set and change encryption keys securely.
WPA2-Enterprise and WPA2-Personal are two distinct security protocols for Wi-Fi networks. Although both protocols use the same AES encryption algorithm, their user authentication methods differ.
WPA2-Enterprise employs a centralized authentication server to verify user credentials. Upon connecting to the network, the user's credentials are transmitted to the authentication server, which then cross-references them with a database of authorized users. If the credentials are valid, the authentication server responds to the wireless access point, granting the user access to the network.
WPA2-Personal authentication uses a pre-shared key (PSK) that is known to all devices connecting to the network. Users are prompted to enter the PSK when connecting to the network. If entered correctly, the user is allowed to connect.
WPA2-Enterprise is considered more secure than WPA2-Personal because it utilizes a centralized authentication server. This means that even if an attacker manages to compromise the wireless access point, they will not be able to access the user's credentials. On the other hand, with WPA2-Personal, which relies on a pre-shared key, if an attacker obtains the PSK, they will be able to gain access to the network.
WEP, WPA, and WPA2 Comparison
|
Feature |
WEP |
WPA |
WPA2-Enterprise |
WPA2-Personal |
|
Encryption |
RC4 |
TKIP |
AES-CCMP |
AES-CCMP |
|
Authentification |
Open system or public key |
EAP/802.1X |
EAP/802.1X |
PSK |
|
Session key size |
64-bit/128-bit |
256-bit |
256-bit |
256-bit |
|
Encryption key |
Static shared key |
Dynamic keys created with RC4 |
Dynamic keys created with AES |
Dynamic keys created with AES |
|
Vulnerabilities |
The encryption keys are weak, and there is a lack of key rotation. |
Vulnerability to TKIP attacks |
Modification of the 4-way handshake is possible |
The security of a shared PSK can be compromised |
|
Security |
Weak |
Moderate, but not sufficient |
Strong with authentication server |
Strong, but risky due to PSK |
What Comes after WPA2?

WPA3 devices, which became widely available in 2019, are backwards compatible with devices using the WPA2 protocol.
WPA3 is designed to replace WPA2 by improving password-based authentication methods and requiring stronger ciphers like AES-GCMP. WPA3 Personal uses randomly generated keys instead of static passwords, while Enterprise integrates 802.1X authentication. Additionally, new WPA3 features address known vulnerabilities in previous standards.
When logging into a public network, WPA3 registers a new device using a process instead of a generic password. WPA3 uses the Wi-Fi Device Provisioning Protocol (DPP), which allows users to authorize devices to enter the network using Near Field Communication (NFC) tags or QR codes. In addition, WPA3 security uses GCMP-256 encryption instead of the 128-bit encryption used previously.
Wi-Fi 6 and 6E offer multi-gigabit speeds but also increase potential vulnerabilities. New protocols can integrate blockchain or machine learning to improve identification, threat detection, and dynamic access control.
Continuous authentication and contextual authorization policies will be crucial for security as wireless technology expands into new industries, such as industrial IoT, telemedicine, and autonomous vehicles.
WPA2 has become the standard Wi-Fi security protocol for securing wireless networks. However, additional tools such as VPNs, proxies, and Tor can enhance network security.
Virtual Private Networks (VPNs) improve the security provided by standard Wi-Fi protocols. A VPN routes and encrypts your traffic through a remote server, keeping your online activity hidden from your ISP, the government, hackers, and other intruders. It also enables safe use of public Wi-Fi and helps you avoid geo-blocking.
VPS
Choose the suitable configuration and enjoy all the benefits of a virtual private server.
From $4.99/moPersonal VPN
Stay anonymous online with a dedicated IP and don't endanger your personal data.
Get $5.00/mo