The ingenuity of cyber criminals is nothing new, which is why many people are now familiar with hacking by brute-forcing passwords. Special bots (programs) that work in automatic mode allow hackers to infiltrate a network by exploiting any vulnerability.
Therefore, when it comes to securely connecting to a remote server, a more secure method than a simple password is required. SSH can provide the necessary level of protection.
What is SSH?
SSH stands for Secure Shell. It is a cryptography-based network protocol used for secure remote access to computers and servers. The technologies used in SSH provide a secure channel between client and server by encrypting all data transmitted, including passwords and commands.
How do I use SSH?
SSH allows users to securely log into a remote system and execute commands as if interacting directly with the local machine.
An SSH server and an SSH client are required to connect via SSH. The SSH server listens for connections on the TCP/IP port and authenticates when a client requests a connection, then begins serving the client, allowing the user to work with the server. The SSH client is used to log in to the remote machine and execute the necessary commands.
You will also need to create a private key and a public key at the beginning, and then add the public key to the server. The private key is stored by the user and is used to access the server.
Will I have to use the command line?
If you want to connect to a remote server from a Windows operating system, simply install a special utility (PuTTY, SecureCRT, ShellGuard, Axessh or others) on your computer. In this case, all operations are carried out using a graphical interface, with the command line used only in certain cases.
If you are connecting from Linux or MacOS, in addition to installing a special utility (Openssh, kdessh, lsh-client, etc.), you will need the built-in Terminal utility. In the Terminal, you will need to enter commands to connect to the remote server.
What is an SSH key?
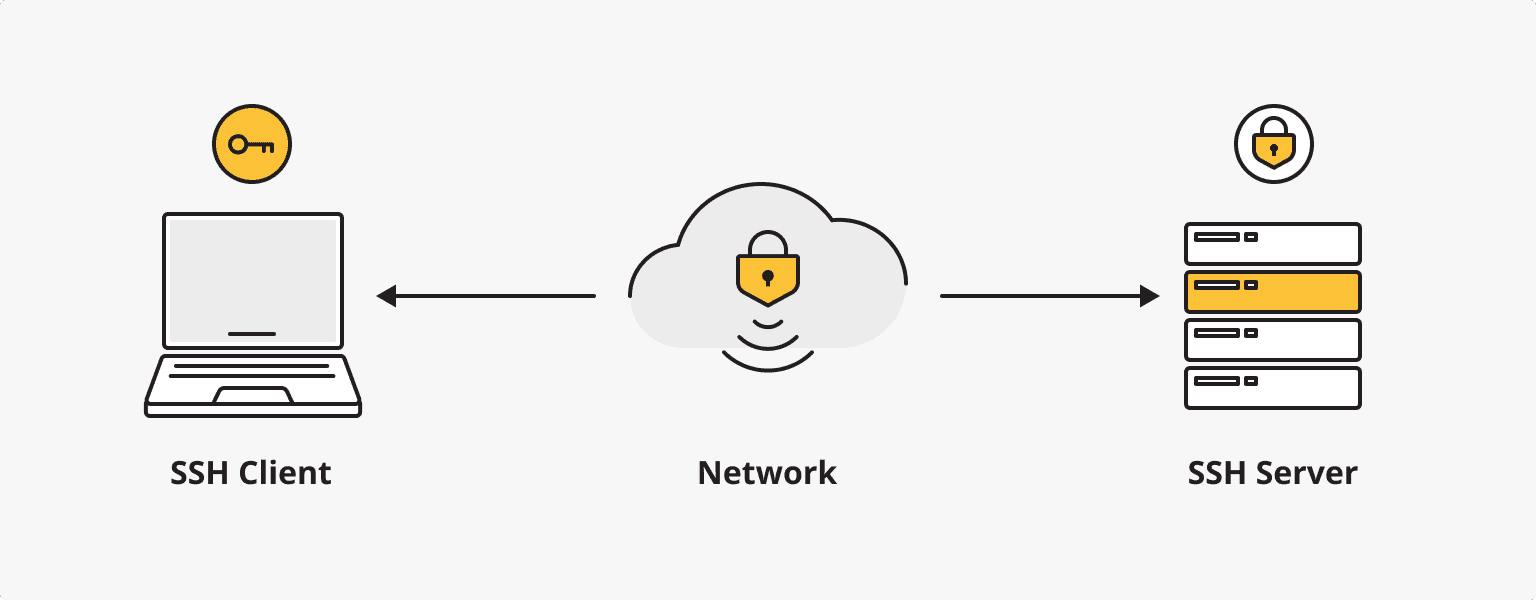
An SSH key is a pair of cryptographic keys used in the SSH protocol for secure authentication. The key pair consists of a public key and a private key. The public key resides on the remote server and the private key is securely stored on the user's computer or device.
When a user attempts to make an SSH connection to a server, the server sends a request to the client. The client uses its private key to create a digital signature, which is sent back to the server. The server can verify this signature using the corresponding public key stored on the server. If the signature is valid, the client is granted access.
SSH keys are a more secure and convenient alternative to traditional password-based authentication. They eliminate the need to transmit passwords over the network and are resistant to brute-force attacks. SSH keys are commonly used by system administrators, developers, and other users who frequently access remote servers.
SSH command examples
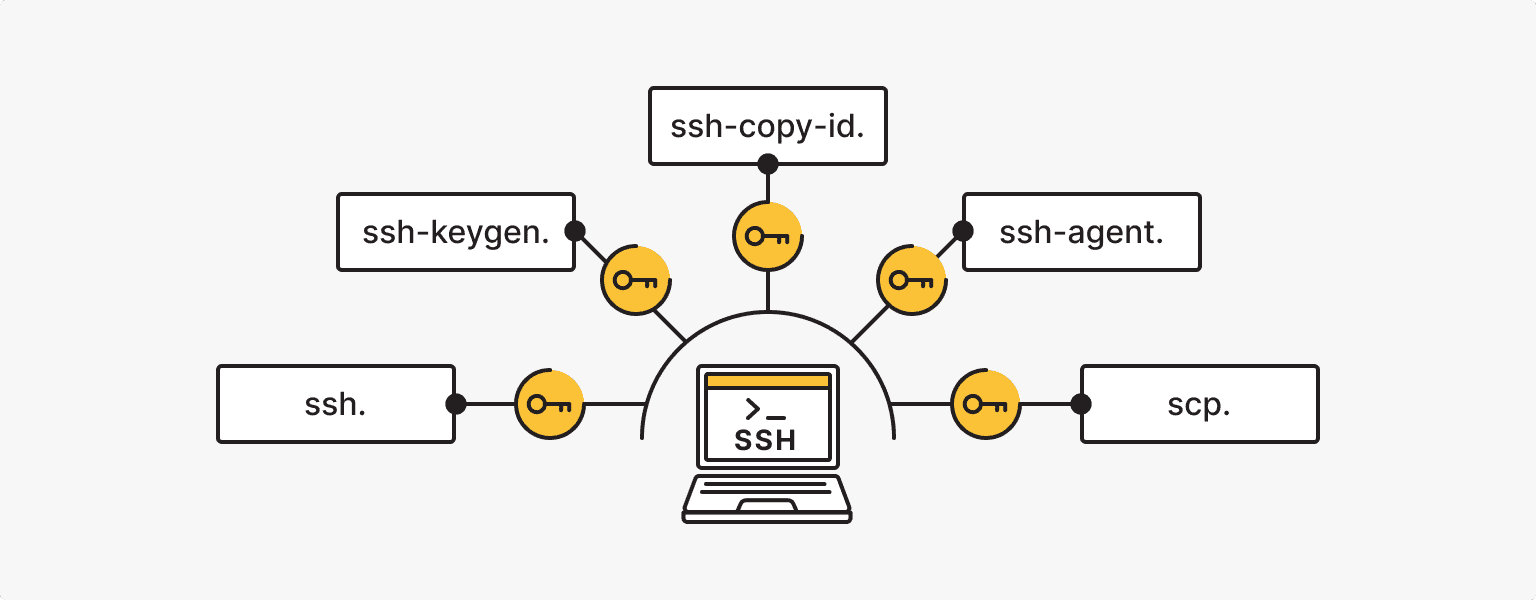
The following commands are used to work directly with the SSH keys:
- ssh. This command is used to establish an SSH connection to a remote server. It usually looks like this: ssh username@hostname.
- scp. The scp (secure copy) command allows for the secure transfer of files between a local machine and a remote server over an SSH connection. It is used as follows: scp [options] <source> <destination>.
- ssh-keygen. This command is used to generate SSH key pairs. It creates public and private key files. The basic syntax is ssh-keygen [options]. For example, ssh-keygen -t rsa generates an RSA key pair.
- ssh-copy-id. After generating the SSH key pair, you can use the ssh-copy-id command to copy the public key to the remote server, providing password-free authentication. This command is used as follows: ssh-copy-id username@hostname.
- ssh-agent. This is the program that manages SSH keys. It stores the decrypted private keys in memory. You can run it with the ssh-agent command and then use ssh-add to add your private key.
SSH also allows you to work with navigation, databases, files, directories, archives, and their contents (create directories and files, copy, move, rename, delete files and directories, etc.). There is also a set of commands for this.
How to enable an SSH connection
Check if SSH is already enabled, as many Linux distributions and MacOS systems install it by default. To check if SSH is enabled, open a Terminal and type the following command
ssh localhost
If you see a message such as "Connection refused" or "Connection timed out", this means that SSH is not currently enabled or configured. If you get a response asking for a password or passphrase, SSH is already enabled.
Set up SSH if necessary. On Ubuntu or Debian-based systems, you can do this by running the command
sudo apt-get install openssh-server
On MacOS, SSH is usually pre-installed.
There is no SSH pre-installed on Windows (e.g. OpenSSH; check for this component via Start - Settings - Applications - Applications and features - Advanced components).
Once SSH is installed, it may need to be configured, but it is possible to leave the default configuration. The SSH server configuration file is usually located in /etc/ssh/sshd_config on Linux systems, /etc/sshd_config on MacOS, and C:\ProgramData\ssh\sshd_config on Windows.
Open the configuration file with administrator rights (sudo nano /etc/ssh/sshd_config) and make any necessary changes:
- Port. By default, SSH listens on port 22. You can change it to another port for security reasons.
- AllowUsers or AllowGroups. Specify here which users or groups are allowed to connect via SSH.
- PasswordAuthentication. Set to "yes" to allow password-based authentication, or "no" to force key-based authentication.
- PermitRootLogin. Set to "yes" if you want to allow the root user to log in via SSH. For increased security, it is recommended to set it to "no" and use a normal user account instead.
Once you have made your changes, save the file and restart the SSH service. On Ubuntu or Debian-based systems, this is the command:
sudo service ssh restart
On MacOS, the SSH service is automatically restarted after the configuration file is saved.
If the firewall is enabled, you will need to allow incoming SSH connections with the command:
sudo ufw allow ssh
To give permission to Windows follow these steps
- Open the Windows Defender Firewall with Advanced Security. You can search for it in the Start menu.
- Click on "Inbound Rules" in the left pane.
- Click on "New Rule" in the right pane.
- Select "Port" and click "Next."
- Choose "Specific local ports" and enter the SSH port number (default is 22). Click "Next."
- Select "Allow the connection" and click "Next."
- Choose the network types for which the rule should apply (e.g., Domain, Private, Public). Click "Next."
- Provide a name for the rule (e.g., "SSH"). Click "Finish."
Once you have completed these steps, you will need to create an SSH key and connect to the remote server using an SSH client.
How to create an SSH key
An SSH key can be generated in a special online service or on a PC using a utility tailored to the operating system (Windows, Linux, MacOS).
SSH key Windows
For Windows, we recommend using the PuTTY utility (the PuTTYgen application is automatically installed to generate the key, download from the official website). The key generation is done inside the application with a clear GUI interface, then the public key (has a .pub extension) must be copied to the server, to the authorized_keys file.
The process of generating and saving a key for Windows is described in more detail in our knowledge base article.
SSH key Linux and MacOS
To create an SSH key on a Linux or MacOS system, we recommend installing the OpenSSH client with two commands in the Terminal (sudo apt update and sudo apt install openssh-client) and the OpenSSH server (sudo apt update and sudo apt install openssh-server). Then continue working in the Terminal:
- Run the command
ssh-keygen -t rsa -b 2048
- Select the path to save the key pair.
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
- Pressing "Enter" will save the keys to the .ssh directory of your home directory.
- If you do not want to enter a passphrase every time you use a private key, just press "Enter".
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
- The key pair has been created. Additional information will be displayed on the screen.
id_rsa is the standard name of the private key file.
id_rsa.pub is the standard name of the public key file. This key must be copied to the servers to which you want to get access when using the private key.
Detailed information on how to place keys on a Linux or MacOS server can be found here.
How to SSH into a server
SSH Linux and MacOS
For Linux/MacOS connections, as with key generation, the built-in Terminal utility is used.
- To establish a connection to the server in the Terminal, run a command with two components: root - login and 192.168.77.77 - IP address of the server:
ssh root@192.168.77.77 - If you are connecting for the first time, you will need to confirm in the pop-up notification and press Enter.
- Enter the password and press Enter.
Done! You are connected to the server.
SSH Windows
To connect to the server using the Windows operating system, you need to log in to PuTTY. This is where we generated the keys.
- In the first window (screenshot below), enter the Host Name (IP address of your server) and Port (default for SSH is 22). If necessary, save the session (Save).
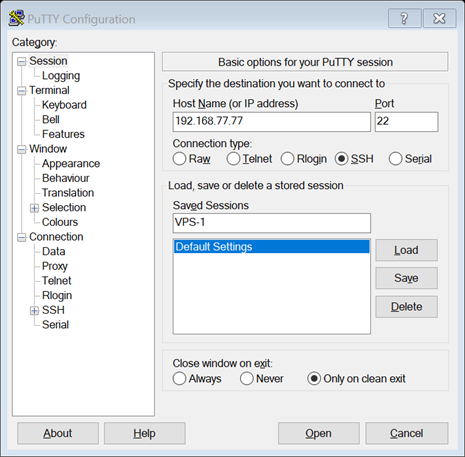
- Then click on Open and Agree in the pop-up window to confirm the connection.
- Enter Login as (root) and Password in the console that opens. Then press Enter.
Done! You are connected to the server.
Best practices for using SSH
- Change the default SSH port for security.
- Implement two-factor authentication.
- Associate SSH keys with individuals, not just a shared account used by multiple users.
- Enforce the principle of least privilege (PoLP) by only allowing access to certain areas.
- Implement a policy for changing SSH keys (do not use the same combination for multiple accounts and sessions).
In general, the steps to securely connect to a remote server using SSH do not end there. The SSH connection itself is more secure than other ways of connecting to a server, and not as difficult to learn.
24/7 Support
Rely on us. is*hosting technical support is available 24/7 and does not ignore customers.
Read More