Social engineering is a serious but often overlooked threat to organizations. While most organizations focus their security efforts on technical vulnerabilities, the human element remains the weakest link. Time and time again, incidents show that a simple phone call to an employee or a cleverly crafted email is all it takes for hackers to penetrate even the most secure networks.
In this article, we'll talk about social engineering and why it's imperative that your organization is aware of this critical risk.
What Is Social Engineering?
Social engineering is the practice of manipulating people to gain access to sensitive information. The main goal of social engineering is to deceive a person in order to obtain valuable information or to force them to do something they would not normally do. It is a form of psychological manipulation that plays on human nature and the desire to be liked, trusted, or useful. Only the manipulator benefits.
History of Social Engineering

The term "social engineering" was first used in the 1960s by a group of sociologists studying ways to influence people to change their behavior. However, the concept of social engineering itself is much older, dating back to the ancient Greeks and Romans, who used rhetoric and persuasion to influence the behavior of their followers and the common people.
In the early 20th century, social engineering was first used by governments and corporations to further their own agendas. This ranges from very clever government propaganda to marketing ploys.
In the 1950s and 1960s, social engineers were hired by companies to develop marketing campaigns that appealed to consumers' emotions and desires. In this way, many companies were able to gain the trust of consumers and even change their minds.
As early as the 1970s, social engineering began to be used for criminal purposes. Criminals use manipulative techniques to trick people into giving them money or personal information. This type of social engineering is now known as phishing.
In the 1990s, social engineering became even more prevalent with the advent of the Internet. Fake websites and emails that appeared legitimate put new users of the global network on notice and forced them to compromise security measures. This type of social engineering is known as spoofing.
Today, social engineering techniques have become more sophisticated. Attackers often impersonate a company's technical support to gain access to accounts or systems. Phishing, a long-standing scam in which users are sent fake emails from a bank or online store to steal information, is also common.
In today's world, social engineering has become a major threat to corporate and personal security. Its methods are constantly evolving, requiring greater awareness of these dangers.
How Does Social Engineering Work?
Social engineering works by exploiting human nature.
- Social engineers can easily flatter people to make them feel good and more likely to trust them.
- Such professionals can do something for a person to make them feel indebted. This makes people more likely to repay the debt in the form of another favor.
- Playing on people's fears by spreading false information to create panic is also applicable to social engineering.
- Social engineers are good at creating a sense of urgency so that victims make a decision without thinking it through. The same goes for a sense of scarcity: "Buy this now; you won't be able to do it later."
- Claiming that someone in a position of power has requested or approved a request for access/information can lower the victim's guard.
- To make people feel the need to comply, social engineers can impersonate authority figures, including law enforcement, bank specialists, etc.
Basic Methods of Social Engineering
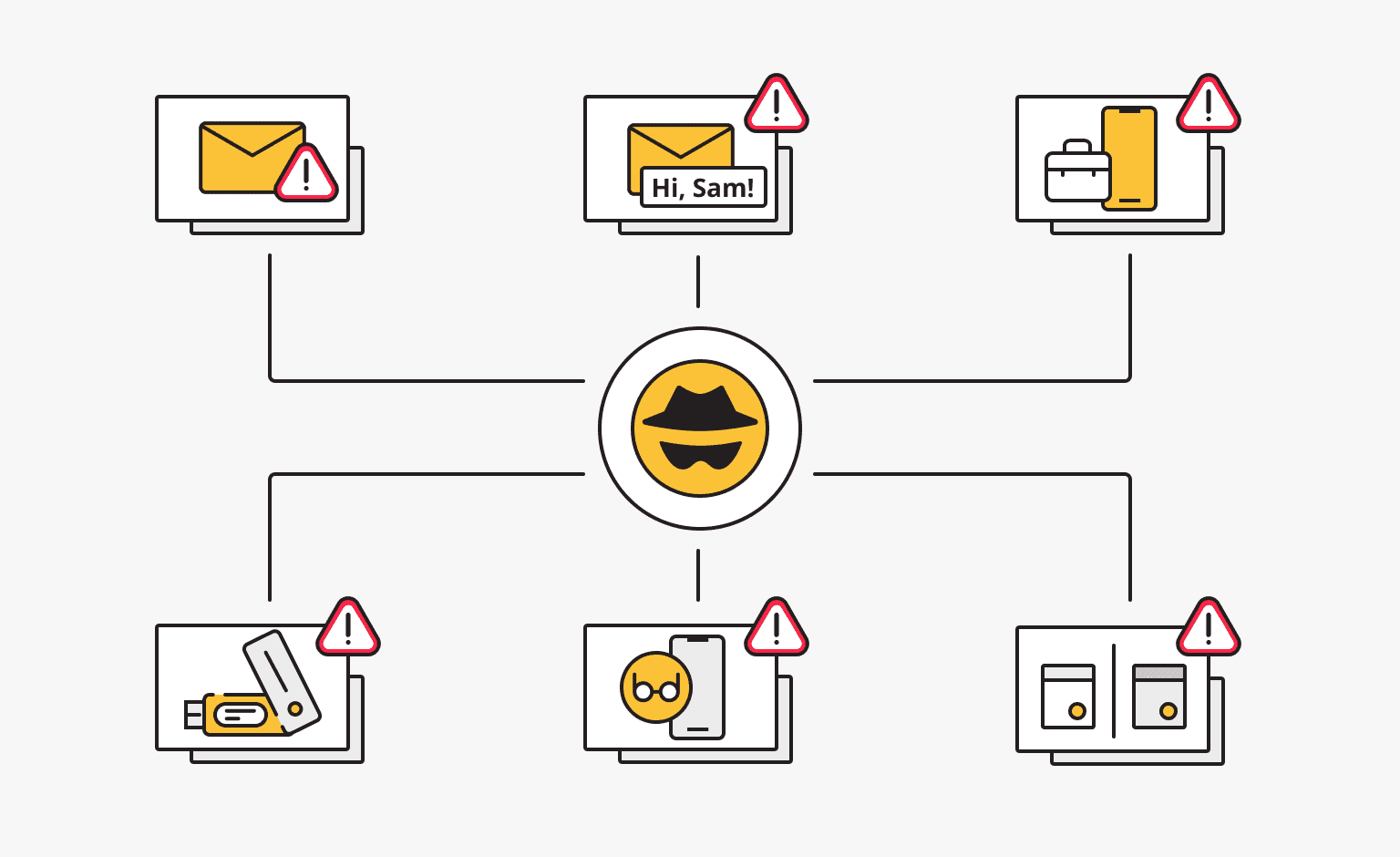
There are many different methods of social engineering, limited only by the ingenuity of those who use them. However, it is possible to highlight the main ones:
- Phishing is a type of attack in which criminals send fake emails or text messages that appear to come from legitimate companies or organizations. These emails or text messages often contain links to bogus websites that look like the real thing. If you click on these links, you may be asked to enter personal information such as your username, password, or bank card number.
- Spear phishing is a type of phishing attack that targets a specific person or organization. Phishing emails or text messages often include the victim's name and information. This increases the likelihood that the person will open the email and click on the links it contains.
- Vishing involves criminals calling people claiming to represent an organization. These criminals may try to trick you into giving them personal information, such as your bank card number.
- Baiting is a type of attack where criminals leave something of value, such as a USB drive, in a public place. If the victim inserts it into their computer, it can give the criminals access to the victim's data or network.
- Spying - stealing information by looking over someone's shoulder as they type in passwords, account numbers, etc.
- Pretexting is a technique in which criminals create a false scenario to trick a person into giving them information or doing something they would not normally do. This attack is similar to vishing or phishing. For example, a criminal may call someone and pretend to be from the IRS and say they owe money. The criminal may then try to get the person to give them their bank card number.
- Spoofing can be defined as an attack where one person or program is disguised as another in order to capture sensitive data. This can include IP spoofing and MAC address spoofing.
Real Social Engineering Examples

Every year, attack statistics show how many millions of dollars citizens and organizations lose to social engineering. For example, attacks that compromise business email will cost U.S. victims more than $2.7 billion in 2022.
No one is immune to an attack, but when corporate employees fail to follow security rules, an attack can cause irreparable damage to many more people.
In 2014, a group known as the Guardians of Peace (GOP) attacked Sony Pictures Entertainment with phishing emails that appeared to be official communications from trusted sources. The GOP tricked Sony employees into revealing their credentials and clicking on malicious links that gave them access to the company's systems.
Once inside, the hackers remained undetected for at least two months, during which time they installed a listening implant, a backdoor, a proxy server, a hard drive destruction tool, and a cleanup tool to remove traces of the attack. They then leaked a massive amount of sensitive data, including unreleased movies (Annie, Fury, and The Interview), confidential business documents, employee records, and private email conversations.
The leaked emails were also particularly damaging because they revealed unfiltered conversations between executives and other industry figures and opinions about celebrities, actors, and business associates.
The identity of GOP remains unknown.
In the case of Sony Pictures Entertainment, we can clearly talk about financial damage to the company and some loss of reputation. The Google Drive case, however, resulted in casualties among ordinary users.
In 2020, scammers exploited a bug in Google Drive to send seemingly genuine push notifications and emails from Google, encouraging Gmail users to click the "Open in Docs" button. Users were then taken to a genuine Google page, where they were asked to give permission for a seemingly legitimate service called "Google Docs" to access their email account data.
Once permission was granted, the scammers gained access to the victim's email account, contacts, and online documents. The malware would then automatically send emails to everyone on the victim's contact list in an attempt to spread itself.
After receiving messages from victims, Google immediately removed the documents used in the scam and patched the vulnerability.
Major cases of social engineering attacks are rapidly spreading across the Internet and causing other companies to think about security measures. But ordinary people are no less vulnerable.
- Google blocks approximately 100 million phishing emails every day.
- More than 48% of emails sent in 2022 were spam.
- In 2021, 323,972 Internet users worldwide were victims of phishing attacks.
- In 2021, the U.S. IC3 received reports from 24,299 victims who lost more than $956 million due to online trust and romance scams.
- Millennials and Generation Z Internet users are the most likely to fall victim to phishing attacks.
- The top 5 most imitated brands in Q1 2022 are LinkedIn (52%), DHL (14%), Google (7%), Microsoft (6%), and FedEx (6%).
- WhatsApp accounts for 90% of phishing attacks sent through messaging apps. Telegram has the next highest percentage, at 5.04%.
Social Engineering Defense
Employee training is a critical part of any organization's security program. Employees must be educated on how to recognize and respond to social engineering attacks. Understanding the importance of protecting their personal information and sensitive company data is an equally critical defense.
Security training should be conducted on a regular basis to keep employees abreast of the latest threats. In addition to training, organizations should foster a culture of security by communicating the organization's security policies and procedures to employees, encouraging employees to report security incidents, and disciplining employees who violate security policies.
Technological defenses that can prevent social engineering attacks on an organization's network and data are also necessary. However, it's important to note that no single defense is 100% effective, which reinforces the need for a combination of defenses.
Anti-social Engineering Technology Solutions
Server technologies such as firewalls and intrusion detection/prevention systems help block malicious traffic and detect suspicious activity from unauthorized sources.
Virtual Private Networks (VPNs) create an encrypted tunnel for all Internet usage, hiding the user's true IP address and location.
How server technologies and VPNs can mitigate risk:
- Firewalls block unauthorized ports/protocols, preventing hacking tools from entering the network. They also filter inbound/outbound traffic according to the organization's policies.
- IDS/IPS systems constantly monitor traffic for suspicious patterns that may indicate social engineering, such as mass emails or data exfiltration attempts. They can alert security services to potential problems.
- VPN encryption encrypts all transmitted Internet data, making it unreadable if intercepted by threat actors. Even if sensitive information is obtained, it is useless without a decryption key.
- Hiding the actual IP address/location with a VPN helps protect against risks such as phishing, man-in-the-middle attacks, and public WiFi sniffing that can expose personal/organizational data.
- Server-side technologies provide an additional barrier to more vulnerable client applications/devices.
Conclusion
Protecting yourself from cybercrime is as simple as having a strong password, following email security best practices, encrypting data traffic, raising employee awareness, and using security technology. In many cases, simply following these rules can make the difference between getting hacked and not getting hacked.
As attackers have become more sophisticated, so has the technology used to fight them. Intrusion detection systems and artificial intelligence-enabled firewalls are at the forefront of defending against today's cyber threats. They are capable of analyzing massive amounts of data to detect anomalies, patterns, and breaches in real time.
But as powerful as these technologies are, they cannot protect us from resourceful criminals on their own. That's why you must make it a priority to educate your employees and build a robust "human" firewal.
Personal VPN
Stay anonymous online with a dedicated IP and don't endanger your personal data.
Get $5.00/mo