- What is cryptojacking and how does it work?
- Cryptojackers: who they are and how they benefit from using other people's devices
- Signs of cryptojacking
- How to prevent cryptojacking: tips and best practices
- How to detect cryptojacking
- Real-life examples of cryptojacking
- The impact of cryptojacking on cybersecurity
Phishing, DDoS attacks, viruses and more have become commonplace in the news — and as threats to people struggling with cybersecurity. As technology advances, so do the dangers not only for online project owners, but also for ordinary users. Today, it is possible to be a victim of cryptojacking and not even know it.
The cryptojacking boom came in 2018, when CoinHive created computer code software to use power from unsuspecting users' devices.
What is cryptojacking and how does it work?

Cryptojacking is a type of cyber attack in which a hacker uses the victim's computing power to mine cryptocurrency without their knowledge or consent. This is done by infecting the victim's device with malware, which is then used to solve complex mathematical problems and generate cryptocurrency profits for the attacker.
There are two main types of cryptojacking:
- Browser-based cryptojacking uses malicious JavaScript code that is injected into a website. When a user visits the website, the code automatically runs in the user's browser and starts mining the cryptocurrency.
- Software-based cryptojacking is the installation of malicious software on a computer or other device. Such software can be disguised as an ordinary application or bundled with other software. Once installed, the cryptojacking software runs in the background and uses the victim's device resources to mine.
In addition to these two basic types, there are other varieties of cryptojacking. For example, some attackers may use social engineering techniques to trick victims into downloading and installing their software, or they may use phishing emails to spread a link to download the software.
Typically, cryptojacking comes down to this pattern:
- A victim visits a website infected with a specific code or clicks on a suspicious link to download an application;
- A mining script automatically runs in the background on the device, controlling its performance and being used to earn cryptocurrency;
- The hacker monitors the operation of the code/software and their own profit from using someone else's device.
Cryptojackers: who they are and how they benefit from using other people's devices
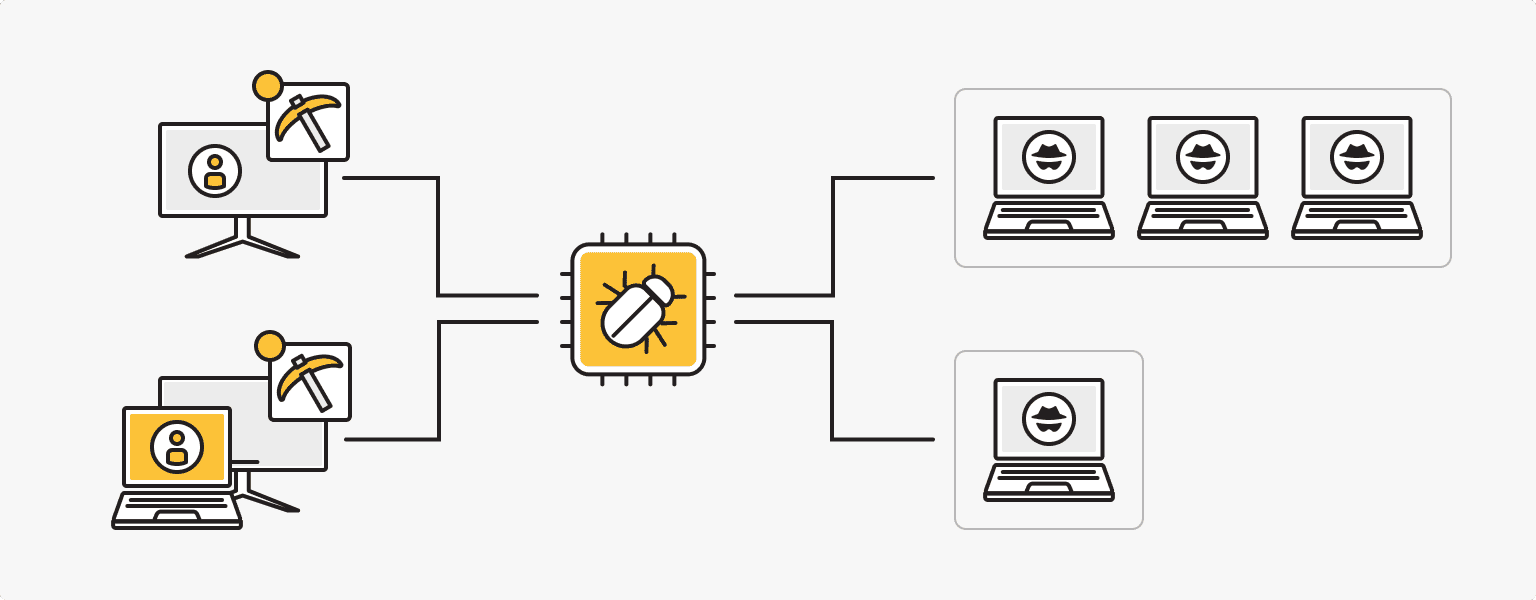
Cryptojackers use a variety of tactics to infect computers and mine cryptocurrency, and can be individuals or organized groups.
Cryptojackers typically use botnets, which are networks of compromised computers that are under the control of an attacker. A botnet can be used to distribute malware and coordinate mining operations, allowing attackers to maximize their profits.
The explanation for this type of mining is very simple. According to the Cambridge Electricity Consumption Index for bitcoin, one of the largest cryptocurrencies, the annual energy consumption of bitcoin in April 2022 was approximately 158 TWh.
To compare, let us look at the estimated annual electricity consumed by some of the world's largest cities:
- Tokyo: 54 TWh
- New York: 56 TWh
- London: 42 TWh
- Beijing: 55 TWh
- Los Angeles: 20 TWh
- Paris: 11 TWh
- Moscow: 26 TWh
If we estimate bitcoin's annual electricity consumption, we can say that the cryptocurrency uses 432 GWh every day.
All figures presented are approximate as they may differ from future and current values. The energy used to mine bitcoin depends on several factors, including the price of electricity, the efficiency of the mining equipment, and the complexity of the mining process.
Cryptocurrency mining is expensive, not only in terms of energy consumption, but also in terms of equipment costs. Therefore, it is much more profitable for miners to infect your device with malware and use its power for free.
Signs of cryptojacking
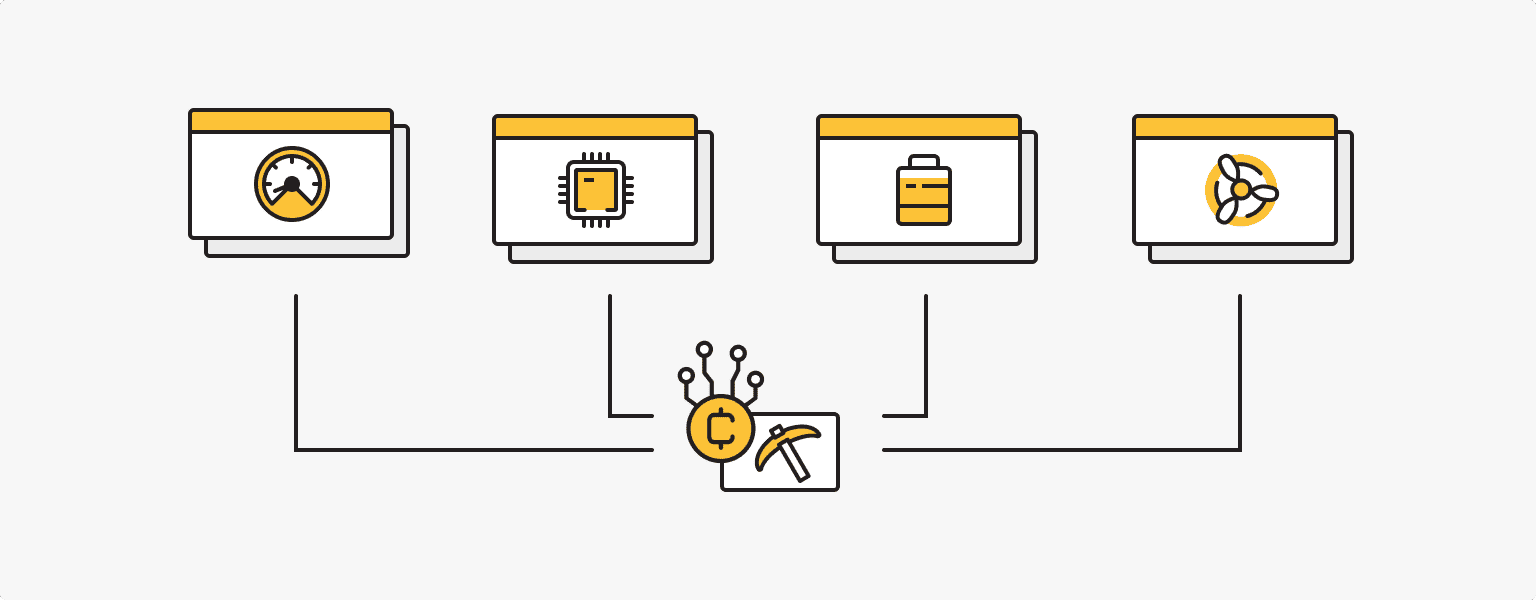
Slow device performance. Cryptojacker malware uses your computer's processing power to perform large amounts of data processing and cryptocurrency mining in the background, which can slow down your computer.
CPU overload. You may find that your computer's CPU load is abnormally high, even when you are not running any intensive programs or applications. This is a clear indication that some software is using most of the CPU power.
Increased power consumption. Rapidly draining a computer can also be a sign that it is being used by malicious individuals. If you have not noticed your battery draining quickly before, or if you have recently replaced it and the problem persists, consider the possibility of cryptojacking.
Excessive load on the device's fans. The fans may be noticeably 'noisy' and constantly trying to cool the computer, even when you are not running resource-intensive programs, if the computer is running third-party tasks in the background.
Unusual network activity. Cryptojacking malware can communicate with external servers to receive mining instructions and send the mined cryptocurrency to the attacker.
How to prevent cryptojacking: tips and best practices
You can protect your computer or device from cryptojacking and other types of malware attacks by following these tips.
Use special software and browser add-ons
There are a number of software and browser extensions that can help protect your computer or device from cryptojacking attacks. These tools can detect and block cryptojacking scripts and malware, and provide real-time protection against future attacks. Ad blockers can also prevent your device from being infected.
You can try ESET Internet Security, Bitdefender Total Security, Malwarebytes Premium, Kaspersky Internet Security and Avast Antivirus. As for browser extensions, you can use MinerBlock, Qualys BrowserCheck, CoinBlocker and others.
Use strong passwords and don't skip updates
Updating your software and operating system is important to prevent all types of malware attacks, including cryptojacking. It is also important to use strong, unique passwords for all your online accounts to prevent unauthorized access to your device. You should also regularly check the operation of the software you use, especially if it was downloaded from the public domain.
Avoid suspicious sites and downloads
Many cryptojacking attacks use infected websites and downloaded files. Be careful when clicking on links or downloading attachments in emails from unknown senders. It may be worth running a scan with the antivirus and other security software mentioned above before downloading an application.
Block websites that have been "caught" by cryptojacking
To prevent cryptojacking when you visit websites, make sure that every website you visit is on a white list. You can blacklist sites known to be cryptojacking. However, this will not give you complete protection.
How to detect cryptojacking
A malware code running in the background is difficult to find, but not impossible. If you have found all the signs of a cryptojacker attack, you should check your device more thoroughly.
Monitor CPU usage and traffic
High CPU load, fan noise, poor performance, and/or the presence of unusual network traffic can be signs of cryptojacking. Use utilities such as System Monitoring to detect programmes running in the background and using more resources.
Install tracker software
There are a number of specialized tools that can help detect and prevent cryptojacking. These tools can scan your computer or device for cryptojacking scripts and malware, and provide real-time protection against future attacks.
These are essentially the same programs we recommended earlier. Simply install them on your computer and run a system scan. The software will then tell you how to get rid of the 'pest'.
Disable JavaScript
Most cryptojacking scripts are written in JavaScript, so disabling JavaScript in your browser can help prevent cryptojacking attacks. However, it can also affect the functionality of some websites, so this solution may not work for everyone. In any case, you should be able to compare the performance of your own device before and after disabling JavaScript. Also remember that hackers can be more inventive with scripting.
Real-life examples of cryptojacking
Cryptojacking is a relatively recent phenomenon. However, the number of companies that have fallen victim to hacker miners is staggering and demonstrates that almost no one is 100% secure.
Coinhive created a popular cryptojacking script that was used by cybercriminals to mine the Monero cryptocurrency. In 2017 and 2018, it was reported that UK, US and Canadian government websites, as well as some media websites (such as the Los Angeles Times and PolitiFact), were infected with the CoinHive script without their knowledge. All visitors to these sites automatically became pawns in the hands of unscrupulous miners.
Another example is hackers hijacking the resources of Tesla's cloud environment to mine cryptocurrency. The hackers used a method similar to cryptojacking, but on a much larger scale. Malware was discovered in the Amazon Web Services infrastructure, resulting in little data exposure and huge energy bills.
In 2019, cybersecurity researchers discovered a new type of cryptocurrency mining malware on Android devices. The software, known as 'ADB.Miner', was spread through infected apps and was able to mine several different types of cryptocurrency.
The impact of cryptojacking on cybersecurity
Cryptojacking, as one of the major forms of cyber attack, has inevitably led to a reaction and appropriate actions being taken by companies responsible for cybersecurity. It is necessary to provide users with reliable protection against existing attacks, and also to predict trends in the hacking software market.
To counter these trends, cybersecurity experts are developing new tools and techniques to detect and prevent cryptojacking attacks. This includes the development of specialized software and browser extensions that can block cryptojacking scripts, as well as the use of machine learning algorithms to detect specific behaviors.
It is also important that companies invest in employee training and awareness programmes to help users recognise and avoid phishing emails and other forms of attacks.
Some experts point out that hackers can use the same "entry point" into a device not only for covert mining, but also to use the owner's confidential information. This raises the question of comprehensive device and data protection.
- What is cryptojacking and how does it work?
- Cryptojackers: who they are and how they benefit from using other people's devices
- Signs of cryptojacking
- How to prevent cryptojacking: tips and best practices
- How to detect cryptojacking
- Real-life examples of cryptojacking
- The impact of cryptojacking on cybersecurity