In the modern digital world, where information plays a crucial role, data protection and privacy become increasingly important. In this context, cypherpunks and crypto-anarchists emerge as technical pioneers, developers of innovative cryptographic methods, and advocates for information security.
In this article, we will discuss the technical achievements of cypherpunks and crypto-anarchists and their fight for digital freedom.
Who are cypherpunks and crypto anarchists?

In the late 1980s, a movement emerged as the epicenter of ideas and revolutionary concepts in the field of cryptography and computer technologies. This movement was called "cypherpunks" and brought together cryptographers, hackers, and activists who aimed to use computers and networks as tools for liberation from control and surveillance by governmental entities.
Cypherpunks sought to change the established order in the digital world by advocating for decentralization and anonymity. They championed information freedom and individual privacy. Essentially, cypherpunks created alternative structures and tools that enabled people to exchange information and conduct transactions while bypassing governmental and centralized control systems.
Cypherpunks and cryptoanarchism are closely related movements. Both movements strive for liberation from state control and aim to establish privacy, freedom, and self-governance in the digital world. Although these terms can be used interchangeably, they have their own nuances and shades of meaning.
Cypherpunks, first mentioned by hacker and programmer Eric Hughes, focus on using cryptography and technical means to ensure personal privacy and security in the digital realm. They aim to protect personal data and ensure the impenetrability of information from unwanted access and surveillance.
Cryptoanarchism is a broader concept that encompasses the use of technology for liberation from the control of state institutions and the establishment of new forms of social organization. Crypto-anarchists believe in using cryptography, anonymous pseudonyms, and digital money to circumvent censorship, surveillance, and taxation.
What is Crypto anarchism and its connection to cryptography and anonymity
Crypto anarchists are a group of individuals who have embodied the strategies of cypherpunks by using cryptography in their activities. The term "crypto anarchy" was first coined by one of the founders of cypherpunks, Timothy C. May, in his "Crypto Anarchist Manifesto".
At the core of the crypto anarchy manifesto and the broader crypto-anarchist movement is a desire to disrupt existing economic and political systems using secure online encryption technologies, with a focus on decentralization and autonomy. Crypto anarchists advocate for privacy both online and offline, particularly in the realm of communications, and fiercely oppose censorship and government and corporate surveillance. They explore the possibilities of anonymity and pseudonyms as a means to overcome these issues.
One of the key ideas of cryptoanarchism is the use of digitally secured cryptocurrencies. Cryptocurrencies like Bitcoin offer the ability to conduct anonymous and untraceable financial transactions without the intervention of banks or governmental institutions. This provides people with greater financial freedom and control over their finances while ensuring confidentiality and circumventing restrictions.
The development of the cypherpunks and crypto anarchists movement

The cypherpunks, although not initially called by that name, found inspiration in the ideas of David Chaum, who introduced the concept of blind digital signatures in 1982, which became the basis for public-key cryptography. This method opened up new possibilities for preserving anonymity and ensuring the authenticity of transmitted information. These ideas attracted a group of cryptographers, hackers, and activists who later became known as cypherpunks.
One of the important ideologists of the movement was Timothy May, an American cryptographer and former senior scientist at Intel. In 1987, he met Philip Salin, an American economist, and entrepreneur who founded the American Information Exchange (AMiX), an online platform for data trading. However, May was not fond of the idea of an electronic marketplace where people could sell insignificant information to each other. He dreamed of creating a global system that would enable an anonymous two-way exchange of any information and resembled a corporate information system.
It was May's acquaintance with David Chaum's ideas, particularly his article on identification-free security systems, that pushed May to study public-key cryptography. Through his research and contemplation, May came to the conclusion that cryptography, combined with networked computing, had the potential to "erode the structures of social power." In September 1988, he wrote the "Crypto Anarchist Manifesto", which was based on Karl Marx's "Communist Manifesto."
In this manifesto, May and his supporters claimed that information technologies would allow people to govern their lives without government interference, using cryptography, digital currencies, and other decentralized tools. In 1992, May, along with John Gilmore, one of the founders of the Electronic Frontier Foundation, and Eric Hughes, a mathematician from the University of California, Berkeley, organized an unofficial gathering that invited their close friends. During this meeting, they discussed pertinent issues in cryptography and programming. These meetings started to be held regularly and laid the foundation for the cypherpunk movement.
They created an email mailing list to attract other individuals who shared their interests and values. The mailing list became a platform for testing ciphers, exchanging ideas, and discussing new developments. Correspondence was conducted using state-of-the-art encryption methods, including Pretty Good Privacy (PGP). Group members actively discussed politics, philosophy, computer science, cryptography, and mathematics.
Over time, the mailing list became popular and attracted more participants. In 1995, Julian Assange, the creator of WikiLeaks, published his first post in "Cypherpunks." In 2016, he released a book titled "Cypherpunks: Freedom and the Future of the Internet" in which he talked about the Cypherpunks movement.
The cypherpunks and crypto-anarchists movement continued to evolve and influence the field of cryptography and decentralized technologies. Their ideas of confidentiality, anonymity, and cryptographic protection found reflection in various cryptocurrencies, such as Bitcoin, which offer the possibility of anonymous and secure transactions.
Philosophy and values: freedom, anonymity, and decentralization
The key ideas and ideology of cypherpunks and crypto-anarchists were formulated and articulated in several important publications.
The "Crypto Anarchist Manifesto" was written by Timothy C. May and first published in 1988. In his manifesto, May compared the development of cryptographic methods to the invention of the printing press and emphasized that they would completely change the nature of corporations and government interference in economic transactions. A few years later, in his "Cypherpunk Manifesto" (1992), Eric Hughes continued this line of thought, outlining the ways in which the movement protects data on the internet: anonymous remailers, electronic money, and digital signatures.
Both manifestos played a crucial role in shaping the ideology of cypherpunks and crypto-anarchists, providing a conceptual foundation and direction for the movement:
- Anonymity and Privacy
Cypherpunks and crypto-anarchists place immense importance on anonymity and privacy in the digital world. They assert that every individual has the right to protect their personal data and communication from unwanted intrusion or surveillance by third parties, including governments and corporations. As Eric Hughes stated in the "Cypherpunk Manifesto": "Privacy is the power to selectively reveal oneself to the world... Anonymity is the power to reveal oneself selectively or to be hidden by default."
- Decentralization and Self-Governance
One of the key ideas of cypherpunks and crypto-anarchists is the creation of decentralized systems where power and control are distributed among network participants rather than concentrated in the hands of central organizations or authorities. They believe in self-governance and social structures based on the principles of cryptography and mathematics. As Timothy C. May wrote in the "Crypto Anarchist Manifesto": "Decentralization is the key to freedom. Only through decentralization can we free ourselves from centralized control and power and create a system where participants make decisions and control their own destiny."
- Freedom of Information and Expression
Cypherpunks and crypto-anarchists place great value on freedom of information and freedom of expression. They assert that access to information and the ability to freely exchange ideas and knowledge are foundational principles of a democratic society. Cryptography and decentralized technologies provide means for protecting and disseminating information independently of censorship and control. As Timothy C. May stated: "Information must be free. It is the key to development, knowledge, and progress. No one should have monopolistic control over information or the ability to suppress the free exchange of ideas."
- Cryptography and Security
Cryptography plays a central role in the ideology of cypherpunks and crypto-anarchists. They see cryptography not only as a means of protecting data but also as a tool for building trust, anonymity, and digital signatures. Cryptographic protocols and algorithms are developed and utilized to ensure confidentiality, integrity, and authenticity of information. As Eric Hughes emphasized: "Cryptography is a tool that allows us to protect our personal data and freedom in the digital world. It creates ciphers that can only be deciphered using mathematics, without relying on trust in third parties."
Privacy and security in the era of digital technologies
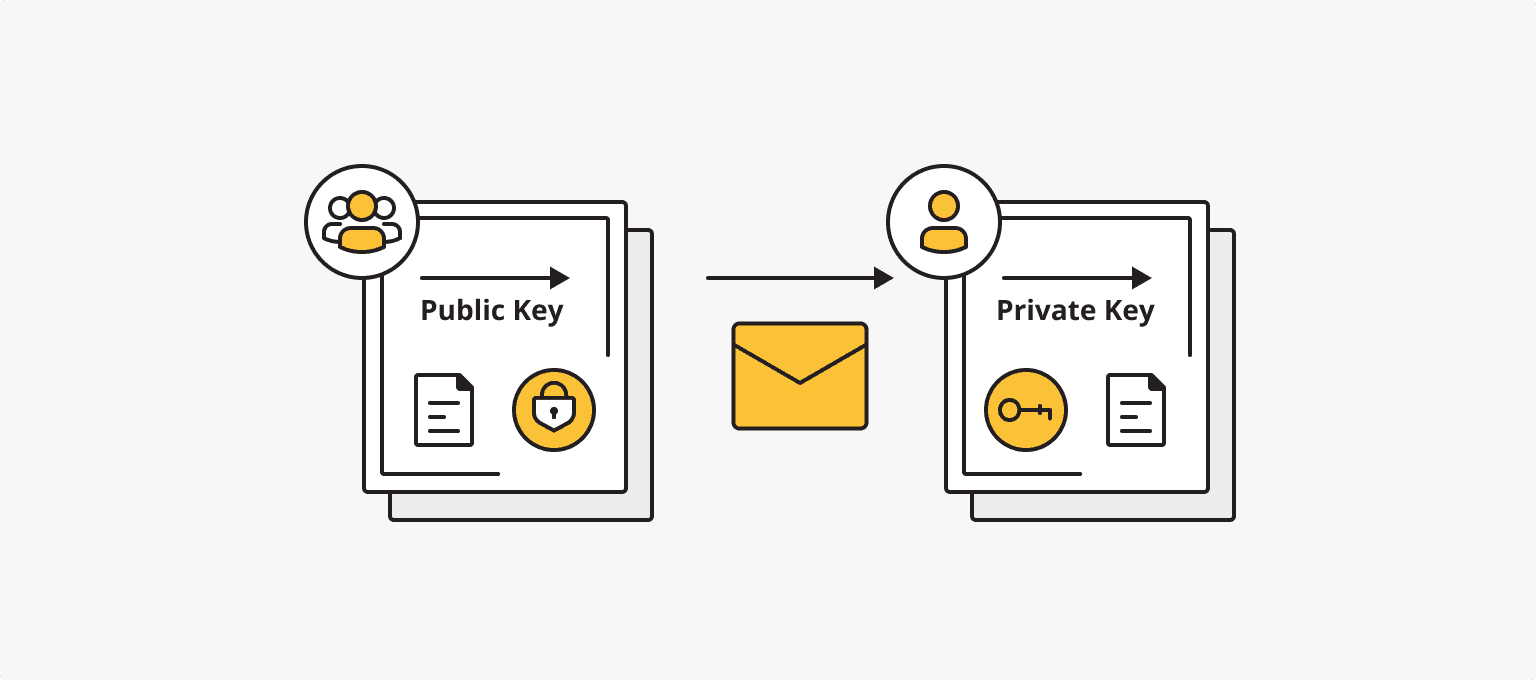
With the development of cyberspace and the increasingly intensive use of online services and digital communications, the issue of privacy and protection of personal data is becoming increasingly critical. More and more people are realizing the need to ensure the security of their personal information and freedom from unwanted surveillance and control by third parties, be it governments or corporations. In this context, cryptography plays a crucial role.
Cryptography is a technique for protecting text that originated in ancient civilizations and continues to evolve and improve to this day. It involves encrypting text in such a way that it can only be read with decryption. Various encryption methods have been used throughout history, from simple letter substitutions to complex mathematical algorithms.
However, primitive encryption methods have their limitations, and with the development of cryptography, more advanced and reliable methods have emerged. In the 1970s, mathematical cryptography emerged, based on knowledge of mathematical statistics, probability theory, number theory, cybernetics, and algorithm theory. The idea of public-key cryptography was developed, where the key for decrypting a message is transmitted over open communication channels.
Crypto anarchists have had a significant influence on the development of cryptography. Their desire to protect privacy and freedom in the digital environment has led to the development and dissemination of new cryptographic technologies and tools.
One of the most prominent examples of the influence of crypto-anarchists on the development of cryptography is the creation of software for encryption and anonymity, such as Pretty Good Privacy (PGP). PGP was developed by Phil Zimmermann, who was an active supporter of the crypto-anarchist movement. PGP allows users to encrypt and sign electronic messages, ensuring confidentiality and data integrity. The proliferation of PGP and similar tools has stimulated the use of cryptography in digital communications.
Crypto anarchists also actively supported and promoted the ideas of open-source software and free software. They saw this as a way to ensure transparency and independence from corporate control, as well as to provide accessibility to cryptographic tools for all users. This contributed to the development and dissemination of various cryptographic libraries, protocols, and programs that are widely used in the field of information security and data protection.
Network security: using Virtual Private Networks (VPN) and anonymous networks (TOR)
In the modern digital world, where threats to security and privacy are becoming increasingly common, it is important to pay attention to tools that can help protect our confidentiality and ensure anonymity in the online space. Two such tools that deserve special attention are VPN (Virtual Private Network) and TOR (The Onion Router).
A VPN is a technology that allows you to create a secure connection between your device and the internet by proxying your internet traffic through a server located in a different location. One of the main advantages of using a VPN is data encryption, which provides privacy protection. When you use a VPN, your internet traffic becomes invisible to third parties, including internet service providers, governments, and malicious actors who may try to track your online activities. VPNs also allow you to bypass geographic restrictions, which is useful for accessing content that may be unavailable in your region.
One of the most reliable ways to ensure privacy and security online today is through the use of a personal virtual private network (VPN). VPN operates based on your own server and provides an encrypted connection between your device and the internet.
Personal VPN
For those who want to remain undetected online and secure their data. Dedicated IP and complete anonymity.
TOR is a free network that allows for anonymous information exchange on the internet. It is based on the principle of multi-layer encryption, where your internet traffic is routed through several nodes called "TOR nodes" before reaching the final destination. This creates a complex network that makes it difficult to trace and identify your location and online activity. TOR also provides access to blocked or censored websites, which is particularly important for users in countries with limited access to information.
Jacob Appelbaum, a prominent cyber activist, hacker, and programmer, played a significant role in the development and popularization of the TOR browser. His contribution to the TOR project was crucial as he worked on various aspects of security and anonymity in the network.
Jacob Appelbaum focused his attention on improving the TOR protocol, which provides encryption and traffic redirection through multiple nodes, ensuring user anonymity and protection against surveillance and tracking.
Although crypto-anarchists and cypherpunks did not directly promote the ideas of VPN and TOR in their ideology, their beliefs and commitment to privacy and anonymity parallel the principles of using these tools. Thanks to their ideas and innovation, we can use powerful tools that provide data encryption, IP address masking, and protection against surveillance, giving users the ability to bypass geographic restrictions and censorship. VPN and TOR have become the realization of concepts advocated by crypto-anarchists and cypherpunks, offering users the ability to control their digital privacy and maintain anonymity in the online space.
Cypherpunks and cryptocurrencies: development of cryptography and anonymous operations
Cryptocurrencies and anonymous operations have become an integral part of the digital world, and their development is closely linked to the ideas and work of cypherpunks.
In 2004, Hal Finney, a renowned cryptographer, and programmer, introduced the technology of reusable proof-of-work (RPOW), based on the ideas of Adam Back, the creator of Hashcash. This technology used cryptographic tokens that could only be used once. This principle is similar to unspent transaction outputs used in Bitcoin network transactions. However, the problem of preventing double spending remained.
Hal Finney is also a candidate for the role of Satoshi Nakamoto, the creator of Bitcoin. He received the first transaction from Satoshi and actively participated in the early development of the cryptocurrency. Finney was one of the first to install and run Bitcoin software and made significant contributions to the discussion and fixing of bugs in the network.
In 2005, Nick Szabo, a computer scientist, and cryptographer, presented the concept of Bit Gold, which later became the foundation for many cryptocurrencies and blockchain projects. Bit Gold incorporated elements of mining and cryptography, which were implemented in Bitcoin. However, the most unique feature of Bit Gold was that each coin within the system was indivisible and had its own value based on the resources spent to create it.
Finally, in 2008, under the pseudonym Satoshi Nakamoto, a technical document was published describing the concept of the Bitcoin network. In this document, Nakamoto referred to Hashcash and b-money, technologies and ideas developed by Adam Back and other cypherpunks. He proposed a new model of privacy where the identities of the sender and receiver of a transaction remained unknown, but all actions were open and visible.
Thus, the development of cryptocurrencies and anonymous operations is closely linked to the ideas and work of cypherpunks and crypto-anarchists. They have made significant contributions to the development of cryptography, anonymity technologies, and security, as well as created fundamental concepts on which modern cryptocurrencies and blockchain systems are based.
The future of cypherpunks and crypto anarchists
The future of the cypherpunk and crypto-anarchist movements remains uncertain and depends on several factors, including the development of technologies, changes in the political and social environment, and society's response to these movements. On one hand, advancements in modern technologies can provide new tools and opportunities for followers of cypherpunk and crypto-anarchist ideas. For example, the use of cryptography and decentralized systems like blockchain may continue to attract people seeking privacy and data protection.
However, progress in cryptography and security can also lead to the development of countermeasures by government agencies and commercial interests. The desire to disclose and regulate cryptographic protocols can have a negative impact on access to the secure and private tools currently in use, potentially violating the fundamental principles of confidentiality and anonymity on which these tools are based.
Advancements in modern technologies: threats to security and privacy in cryptography
The modern development of technologies such as quantum computers and artificial intelligence (AI) introduces a range of new possibilities and advantages across various aspects of our lives. However, along with these new achievements, serious threats to the principles of security and privacy on which cryptography is based also arise.
Quantum computers have the ability to solve complex mathematical problems significantly faster than traditional computers, posing a threat to many existing cryptographic algorithms. For instance, Shor's algorithm, designed for quantum computers, can break RSA, which is widely used for data encryption and digital signatures.
This means that if quantum computers reach a sufficient level of development, existing encryption systems and cryptographic protocols could be compromised. Private data, financial transactions, and confidential information would become vulnerable to unauthorized access.
Artificial intelligence (AI) plays an increasingly important role in various domains, including blockchain, Bitcoin, and encryption. However, in blockchain and Bitcoin, where transactions are recorded and publicly available, AI can be used to analyze data and reveal personal information about users, even if it was initially anonymized.
In light of these threats, there is a need for ongoing improvement of security protocols and cryptography that can withstand attacks from quantum computers and artificial intelligence algorithms. New cryptographic algorithms and protocols must be developed with the latest technological advancements and threats in mind to ensure a high level of data security and protection.
Crypto wars and crypto anarchism: competition for privacy and freedom in the digital age
Crypto wars represent a complex and dynamic conflict that arises between government agencies and cryptographic technologies in the pursuit of establishing control over encryption or bypassing it for various purposes. The key issue at the heart of this confrontation is the balance between power and privacy. Governments and law enforcement agencies seek access to encrypted information for investigations and surveillance, while crypto-anarchists insist on the inviolability of privacy and freedom of communication.
One prominent example of the rivalry within crypto wars occurred in 2016 between Apple and the Federal Bureau of Investigation (FBI). The FBI demanded that Apple provide access to the encrypted iPhone of a participant in a terrorist attack in San Bernardino. However, Apple refused to comply with this request, citing the importance of user privacy.
Cryptowars and cryptoanarchism demonstrate that in the digital age, an ongoing battle for privacy, freedom, and control exists, and the protection of privacy becomes increasingly relevant in the context of technological advancements.
Today, many years after the emergence of the cypherpunk and crypto-anarchist movements, their ideas and principles remain relevant. In the era of the digital revolution, followers of these movements continue to seek ways to protect data, privacy, and freedom in the online world. Their contribution to the development of cryptography and computer technologies remains significant, and the movement itself serves as a vivid example of how ideas and beliefs can influence the transformation of digital reality.
Personal VPN
Stay anonymous online with a dedicated IP and don't endanger your personal data.
Get $5.00/mo