With the rise in cybercrime, the privacy of users' data has become a priority, especially for large enterprises. Network security today directly influences the reputation of any business. Today, we will talk about firewalls, their role in network security, the types of firewalls, and what to expect from the next generation.
Definition and Purpose of Firewalls
A firewall is a network security device that monitors and filters incoming and outgoing network traffic. A firewall is an internetwork screen that decides whether to allow or block specific traffic based on an organization's previously established security policies. In this way, a firewall protects network security and acts as a barrier between a private internal network and external networks, allowing non-harmful traffic through and blocking malicious traffic.
Evolution of Firewall Technology
The history of firewalls dates back to the late 1980s when they were born as packet filters, networks created to examine the bytes sent between computers. Firewalls have come a long way in various forms as technology has advanced over the decades.
- In the late 1980s, the development and spread of virus attacks fueled the growth of antivirus products.
- In the mid-1990s, cyberattacks affecting all businesses led to the development of the firewall.
- In the early 2000s, the exploitation of application vulnerabilities influenced most enterprises and provided the basis for intrusion prevention system (IPS) products.
- Closer to 2010, the rise of mysterious, polymorphic attacks in enterprises led to the emergence of anti-bot and sandbox defense products.
- The year 2017 introduced advanced threat prevention solutions for large-scale, multi-vector mega-attacks.
The first stateful firewall, FireWall-1, introduced in 1993, continues to be an organization's first line of defense against cyberattacks. And we'll talk about the multifunctionality of modern and next-generation firewalls in the section on advanced firewall features.
Types of Firewalls: Static Packet-Filters, Stateful Inspection, and Proxy
From the previous section, we have learned that with the advancement of technology, various new types of firewalls have also been developed in such a way as to outperform the previous generations of firewalls. Much of the underlying technology has changed from generation to generation, and firewalls have started incorporating various filtering methods.
Types of firewalls differ in their approach to:
- Filtering rules.
- Connection tracking.
- Audit logs.
Each type operates at a different level of the communication model, the Open Systems Interconnection (OSI) model. This model improves your understanding of how each firewall interacts with connections.
Static Packet-Filtering Firewall
Description: A packet-filtering firewall is a small amount of data that is analyzed and distributed according to filter standards.
These include static packet-filtering firewalls (stateless inspection firewalls) and operate at the OSI network layer (layer 3). These firewalls' filtering is based on IP addresses, ports, and packet protocols, examining all individual data packets sent over the network. Previously accepted connections are not tracked. Each connection must be reconfirmed with each data packet sent. At a minimum, these firewalls prevent two networks from connecting directly without permission.
Filtering rules are set by a manually created access control list. Effective use of static filtering requires constant manual refinement. This may be easy for small networks but difficult for more extensive networks.
The inability to read application protocols means that the contents of the message delivered in the packet cannot be read. Therefore, packet filtering firewalls have limited protection quality.
Stateful Inspection Firewall
Description: Utilizing dynamic packet filtering, the system actively monitors connections to discern and selectively permit specific network packets through the firewall.
This type includes firewalls with dynamic packet filtering (stateful firewalls). They differ from static firewalls in their ability to monitor current connections and remember past ones. They initially operated at the transport layer (layer 4), but today, these firewalls can monitor multiple layers, including the application layer (layer 7).
Like static filtering firewalls, stateful firewalls allow or block traffic based on specific packet protocols, IP addresses, or ports. However, these firewalls are unique in that they monitor and filter traffic based on the state of connections using a state table.
Stateful firewalls themselves update filtering rules based on past connection events recorded in the state table by the inspection router.
Although typically filtering decisions are often based on the administrator's rules when configuring the computer and firewall, the state table allows these dynamic firewalls to make their own decisions based on the interactions they have previously learned. For example, types of traffic that caused disruptions in the past will be filtered out in the future. The flexibility of stateful inspection allows it to be one of the most common types of safety screens.
Proxy Service
Description: A network security system that protects by filtering messages at the level of the application.
A type of proxy service includes proxy firewalls, also known as application layer firewalls (layer 7). They are unique in that they read and filter application protocols. They combine application-level inspection, or “deep” packet inspection (DPI), and stateful inspection.
Unlike other types of firewalls, it acts as two additional hosts between external networks and internal computers, with one serving as a representative (or “proxy”) for each network.
Filtering is based on data at the application level, not just IP addresses, ports, and packet protocols (UDP, ICMP). Reading and understanding FTP, HTTP, DNS, and other protocols allows you to conduct deeper research and cross-filter on many data features.
It is a firewall that inspects and evaluates incoming data. If no problems are found, the data is passed on to the user.
Despite such enhanced protection, sometimes it interferes with incoming data that does not pose a threat, leading to work delays.
Growing threats require increasingly intensive solutions, and future-generation firewalls (new-generation firewalls (NGFW), hybrid firewalls, etc.) do not remain apart from this problem, combining the functions of a traditional firewall and a network intrusion prevention system, and sometimes using two or more types of firewalls on the same private network.
How Firewalls Work: Basic Principles
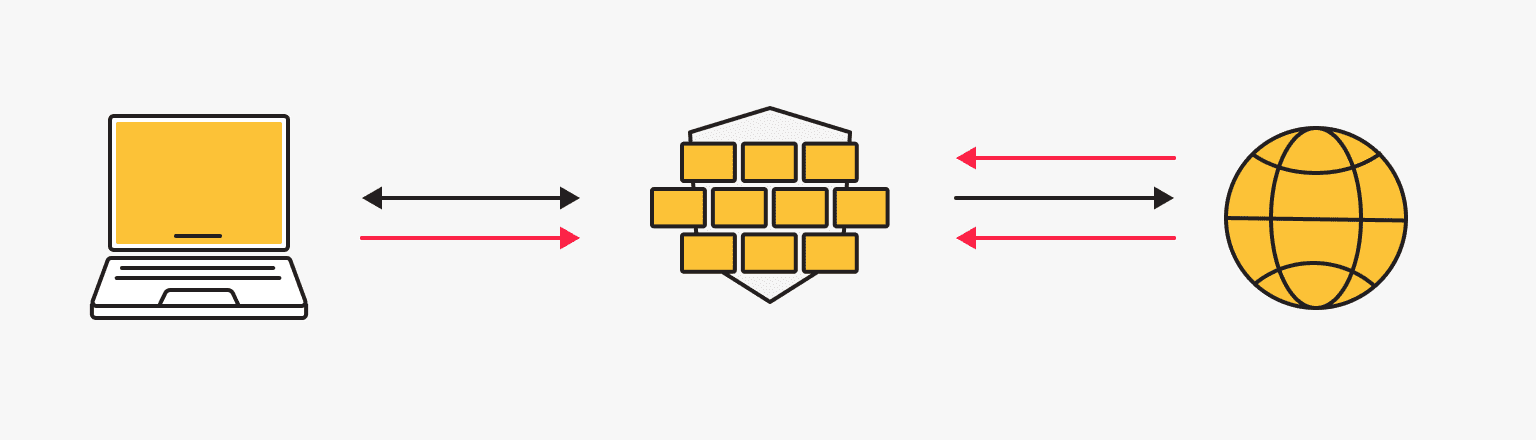
As we mentioned earlier, a firewall is a barrier between a private internal network and a public external network, filtering good traffic from bad, allowing good traffic to pass, and blocking bad traffic. The entire Internet is segmented into:
- External Public Networks: these typically include the public/global Internet or various extranets.
- Internal Private Networks: home networks, corporate intranets, and other “closed” networks.
- Perimeter Networks: these detail edge networks consist of computer hosts dedicated to enhanced security and ready to withstand external attack. They are more secure than external networks but less secure than internal networks and are not always present in simple home networks but are often used in corporate ones.
Firewalls control traffic at computer entry points, called ports, through which information is exchanged with external devices.
At the network layer, firewalls use two routers: one is known as the access router between the external network and the perimeter network, and the other router is used between the perimeter and the internal network. This creates three subnets, respectively. Network firewalls come in two most common models: internetwork firewalls and host firewalls.
- Internetwork Firewalls involves using one or more firewalls between external networks and internal private networks and can be in the form of any of the following types of devices: dedicated hardware, software, and virtual.
- Host-based Firewalls, also known as “software firewalls", protect individual user devices and other private network endpoints and receive individual traffic control from specific computer applications. Host-based firewalls can run on local devices as an operating system service or an endpoint security application. Host firewalls can also dig deeper into web traffic, filtering it based on network protocols, allowing you to control the type of content and control where it comes from.
If the network firewall requires the configuration of numerous connections, then the host firewall can be configured according to the needs of each device. However, networked systems are ideal for complex management solutions because host-based firewalls require more configuration effort. However, using both firewalls simultaneously in both places is suitable for a multi-layered security system.
Firewall Rules and Policies
Traffic filtering using a firewall is carried out according to predefined or dynamically created rules for allowing and denying connection attempts. These rules explain how a firewall controls web traffic through your private network and computers. All firewalls, regardless of which type, filter based on the following parameters:
Source: where the connection attempt is made from.
Destination: where the connection attempt should go.
Contents: what the connection attempt is trying to send.
Protocol packets: What “language” does the connection try to establish to transmit its message?
Among the network protocols hosts use to “talk” to each other, TCP/IP protocols primarily communicate across the Internet and within intranets/subnets.
Application Protocols: Common protocols include HTTP, Telnet, FTP, DNS, and SSH.
The source and destination are transmitted over Internet Protocol addresses and ports, also known as IP. IP addresses are unique device names for each host. Ports are a sublayer of any source and destination host device. When the firewall detects traffic that matches the specified rule conditions, it takes the appropriate action by prioritizing the rules: it applies the rule at the top of the firewall rule list.
- If traffic matches the conditions of this rule, the firewall does not apply any other rules in the list. It allows or blocks this traffic.
- If the traffic does not match the conditions of the top rule, the firewall moves down the list of rules until it finds a rule that the traffic matches.
- If the traffic doesn't match any rules, the firewall automatically blocks it.
Sometimes, intercepted traffic matches several rules from the list. Then, the priority principle is that the firewall only applies the first rule in the list that the traffic matches.
The firewall rules policy places specific rules at the top of the list and general rules at the end. This allows traffic to be filtered properly according to established rules.
Example:
Let's say we want to allow all HTTP requests except those from an IP address in the format “100.100.1.1”. In this case, we need to establish the following two rules, but without fail:
Rule № 1:
Blocking rule – blocking HTTP traffic with IP address 100.100.1.1. This specific rule is a priority, so it should be placed higher on the list of firewall rules in order to specify the general rules at the bottom of the list.
Rule № 2:
Allow rule – Allows all traffic using the HTTP service. This is a general rule that the firewall will match with a specific one, thereby prioritizing it, making that specific rule the priority one, and preventing all HTTP requests from being allowed.
Implementing Firewalls in Different Network Environments
Firewalls are used in both corporate and private networks. Modern organizations include them in their information and security management strategy along with other cybersecurity systems.
Firewalls are often used in conjunction with antivirus applications. Unlike enterprise firewalls, personal firewalls are usually a single product rather than a collection of different products. They may be software-based or a device with built-in firewall firmware.
Here are some options for using firewalls:
- Protection from threats. Firewalls can be installed to protect against external threats or to create segmentation and protection against internal threats.
- Logging and auditing functions. Firewalls keep records of events that help administrators identify patterns and improve rule sets. Regulations must be updated regularly to adapt to constantly evolving cybersecurity threats. Vendors detect new threats and eliminate them in the shortest possible time.
- Traffic filtering. A firewall can filter traffic and alert users to intrusions on the same home network. This is especially useful for always-on connections (subscriber lines or cable modems) since these connections use static IP addresses. The firewall allows only targeted and non-destructive content from the Internet.
- Access control and blocking. Firewalls can be used to control and block access to specific websites and services to prevent unauthorized use. For example, to ensure that employees comply with company policies when surfing the Internet, an organization might use a firewall to block access to inappropriate sites.
- Secure remote access. Firewalls can be used to provide secure remote network access through a virtual private network (VPN) or other secure remote access technology.
How to Choose a Firewall for Your Business
For a home network, at least a primitive antivirus scanning of traffic using known protocols is sufficient, and a simple software solution for installation on the “central” host of the home network or an inexpensive compact hardware solution may be suitable as a firewall. In that case, the situation with enterprises is more complicated. We devoted this section to the main criteria for choosing a firewall for your enterprise.
The proper firewall can help prepare your business for growth by consolidating the number of products you manage, reducing costs and cycles, and making the overall management of your network infrastructure easier and more efficient.
A firewall on a computer network must operate smoothly as part of a comprehensive security system that can cover and adapt to your changing needs. To save time and find the right firewall for your use case, you need to determine the security features that are a priority for your network and organization. Choosing a firewall that can scale as your organization and network grow is important.
Here are a few key considerations when choosing a firewall for your enterprise:
Bandwidth. The bandwidth must match your needs. Your firewall must be able to quickly identify applications and scale to handle and protect growing network traffic demands.
What type do you need? Effectively analyzing traffic in real time requires a much more specialized process than most firewalls can provide. Detecting today's sophisticated cyberattacks involves using more advanced firewalls with advanced functionality.
Durability. To avoid filling gaps every couple of years, it's necessary to make educated guesses about your bandwidth requirements three years from now, double them, and then choose a firewall that’s highly capable of protecting that volume of traffic.
High-performance processor. Traffic analysis is crucial for the firewall processor. You need to ensure that the firewall supports specialized features for effective security inspection and is not built on generic processors that are not designed for this purpose.
Multiple suppliers or one supplier. Taking a multivendor approach adds complexity. Therefore, multivendor solutions should be created using common standards and open APIs to save time and effort.
In contrast, solutions provided by a single vendor, mainly if supported by a common OS, can significantly save time, simplify management, and improve operational efficiency.
NGFW. NGFW selections include decryption, advanced threat protection, content filtering, endpoint integration, sandboxing, IoT visibility and control, remote access, and secure SD-WAN.
Focusing on the security features you most need in a firewall will help you find the right solution.
Popular Firewall Vendors
In order to purchase a firewall, businesses must understand their needs and network architecture. There are many firewall types, features, and vendors, including the following NGFW (Next-Generation Firewall) vendors:
- The Barracuda CloudGen Firewall provides advanced threat protection designed for hybrid cloud environments.
- The Cisco Firepower Series offers malware detection, IPS, URL filtering, and other cloud firewall capabilities built on Kubernetes.
- Fortinet FortiGate offers intrusion protection and other AI-powered services designed for small organizations as well as enterprise data centers.
- Palo Alto Networks PA Series provides machine learning-based threat and intrusion detection. It offers options for SMBs, large enterprises, and managed service providers.
- The SonicWall Network Security series of appliances offers advanced threat protection, URL filtering, malware detection, and intrusion protection.
- The Sophos XG Series offers threat intelligence, intrusion prevention, and firewall protection for web applications for SaaS, software-defined WAN, and cloud traffic.
Firewall Guidelines
Below are some common firewall guidelines that most organizations should follow:
- By default, block all traffic and allow only certain traffic.
- Follow the principle of least privilege and provide users with the minimum level of access necessary to perform their responsibilities.
- Regularly conduct security audits for vulnerabilities.
- Administer Firewall Change Control to manage and track changes to firewall rules.
- Keep your firewall software updated to detect and block any new threats.
- Optimize firewall rules to reduce unnecessary processing and improve performance.
Advanced Firewall Features
Today's businesses rely on technology for everything from communications to server-hosting applications. As technology advances, the attack surface to which cybercriminals have access grows, and cyberattacks become more sophisticated. Thus, organizations are increasing their security posture by seeking to protect every layer of their infrastructure from cyberattacks. In this section, we will provide examples of firewalls with advanced features for deeper inspection, detection, and prevention of cyberattacks.
Intrusion Detection and Prevention Systems (IDPS)
An Intrusion Detection and Prevention System (IDPS) monitors the network for potential threats, preventing possible attacks. The main task of the system is to detect, log, and prevent threats, as well as provide reports. IDPS scans processes for malicious patterns, compares system files, and monitors user behavior and system patterns.
Main functions of IDPS:
- Protects technology infrastructure and sensitive data.
- Checks existing users and security policies.
- Collects information about network resources.
- Helps comply with regulatory requirements.
In most cases, the first step toward meeting these requirements is to install an intrusion detection and prevention system.
Virtual Private Networks (VPNs) and Firewalls
You can also get additional protection by using virtual private networks (VPN). VPN helps expand the functionality of firewalls:
|
Firewall |
VPN |
|
Protects your device or network from external threats. |
Protects your data and identity from prying eyes. |
|
Works at the network level. |
Works at the application level. |
|
Does not encrypt your data or change your IP address. |
Encrypts your data and does not change your IP address. |
However, the main difference between a firewall and a VPN is their orientation. Firewalls are focused on blocking websites. VPN focuses on a private connection, allowing you to access restricted sites through a secure connection.
NGFW and Deep Packet Inspection
The sheer number of entry points and different types of users on modern networks require more stringent access controls and security measures on the host. This need for a layered approach has led to the advent of the Next-Generation Firewall (NGFW).
This type of firewall combines other types with additional software and security devices included in the package. The advantage of NGFW is that it incorporates the strengths of each firewall type to cover another’s weaknesses. NGFW is not just one component but a collection of technologies under one name.
NGFW combines three key assets: traditional firewall capabilities, application awareness, and IPS. NGFWs bring additional context to the firewall decision-making process.
NGFW has the capabilities of traditional enterprise firewalls, including network address translation, URL blocking, and VPN, features not traditionally found in first-generation products. NGFW also uses deep packet inspection (DPI) to inspect packet contents and prevent malware.
Conclusion
In conclusion, we would like to continue the topic of next-generation firewalls. As cybersecurity grows and attacks become more sophisticated, the capabilities and functionality of these firewalls also increase and improve every day, and the next generation of firewalls will continue to be an essential component of any organization's security solution.