What is Lightning Network?
The Lightning Network is a solution designed to address the issues of slow transaction speeds and high costs associated with the Bitcoin blockchain. It serves as a second layer for Bitcoin, enabling transactions to be conducted off-chain through micropayment channels. This innovative technology allows users to directly send and receive payments with each other, bypassing traditional intermediaries such as banks. What are the benefits of the Lightning Network?
The Lightning Network operates by creating payment channels between participants. These channels allow for numerous transactions to occur without relying on the Bitcoin main network to confirm each operation. Instead, participants can transfer funds between themselves within the channel, which provides speed and efficiency in transactions. Upon closing the channel, the final state of the transactions is recorded on the Bitcoin blockchain for verification.
One of the primary goals of creating the Lightning Network is to improve Bitcoin's scalability. As the number of daily transactions increases, there is a need for prompt and cost-effective transaction confirmation. The Lightning Network addresses this issue by enabling many transactions to occur off-chain, reducing congestion on the main network, and increasing transaction speed.
Smart contracts and multi-signatures play a crucial role in the Lightning Network by properly routing funds to recipients. These features provide additional security and reliability for off-chain transactions conducted on the network.
Privacy of the Lightning Network
While the Lightning Network provides a certain level of privacy, it's important to note that it is not designed to provide complete transaction anonymity. However, the network incorporates certain technologies to enhance privacy during transactions:
- Off-chain transactions: Lightning Network transactions occur off-chain, meaning they are not directly recorded on the main blockchain. This provides some privacy advantages since not all transactions are visible to the wider public. However, the opening and closing of Lightning channels and channel balances are still visible on the blockchain.
- Onion routing: To enhance privacy in the Lightning Network, it utilizes a technology called onion routing inspired by the Tor network. When a payment passes through multiple nodes, each node only knows the previous and next node in the route, preventing individual nodes from obtaining complete transaction information.
- Channel-level privacy: Transactions in the Lightning Network occur within payment channels established between participants. Transaction details within a channel are not publicly disclosed. However, participants involved in the channel will have access to information about payments made within that channel.
It's worth noting that additional methods are actively being developed to improve privacy within the Lightning Network. Projects like Eltoo aim to enhance the privacy properties of Lightning channels through more efficient and private updates.
Despite these efforts, achieving complete privacy in any financial system is complex. To enhance privacy and security on the Lightning Network, users should consider additional protective measures, such as using a VPN from is*hosting. This allows you to have a dedicated IP address and maintain maximum anonymity and confidentiality within the network.
Personal VPN
For those who want to remain undetected online and secure their data. Dedicated IP and complete anonymity.
Main Concepts of Lightning Network
Payment Channels
Payment channels are a key component of the Lightning Network. They allow users to conduct an unlimited number of transactions with each other without the need for block confirmations on the blockchain. This approach significantly enhances the speed, efficiency, and cost-effectiveness of transactions in the Bitcoin network, particularly for microtransactions.
A payment channel is a 2-of-2 multisig wallet, meaning funds can only be spent when both parties agree to a transaction. Until the channel is closed, the number of transactions between the users is not limited, and there is no need to broadcast the transactions to the Bitcoin blockchain.
To create a payment channel, two users contribute a certain amount of Bitcoin to a multi-signature wallet on the Lightning Network. This funding establishes a channel or direct connection between the two parties, which can be used for conducting multiple transactions. The initial state of the channel, including the allocated funds, is recorded on the Bitcoin blockchain.
Upon closing the channel, the final state of the smart contract is broadcasted to the Bitcoin network, and the corresponding amounts of Bitcoin are transferred to the users' wallets. Due to the majority of transactions occurring off-chain, with only the net result being settled on the blockchain, the Lightning Network provides fast and secure transactions without needing individual block confirmations.
Multi-hop Payments
One of the key advantages of the Lightning Network is its support for multi-hop payments. This feature allows users to make payments to other parties through a series of interconnected channels involving intermediate network users. In other words, if User A wants to send Bitcoin to User B but they don't have a direct payment channel, they can route the payment through User C, who has open channels with both User A and User B. This interaction enhances the flexibility and scalability of the Lightning Network by expanding the network's reach and reducing the need for direct channels between every user.
Hashed Timelock Contracts (HTLCs)
HTLCs are a central element of any transaction in the Lightning Network and ensure the security of multi-hop payments. An HTLC is an output of an unconfirmed transaction to a separate smart contract address that possesses the following properties:
- The smart contract can be spent by revealing the secret code and a valid recipient's signature.
- The smart contract can be redeemed with a valid sender's signature after a certain time.
- The party presenting the revocation key can immediately redeem the smart contract.
Ideally, this transaction does not need to be recorded on the blockchain. Instead, when the secret code (preimage) is revealed by the recipient, the channel balances can be updated by creating a new commitment transaction and invalidating the previous one.
HTLCs provide security and reliability for transactions across different payment channels. They guarantee that payments will either be fully completed or fully canceled, and no one can seize funds from the payment along the path.
To ensure payment security, all parties involved in the payment route use the same secret code to create their HTLCs. This secret code is hashed to a unique value.
All parties have an interest in the expiration of the HTLCs occurring in a specific order that allows them to be smoothly redeemed. This means that if an HTLC is redeemed by the final payment recipient, the secret code is revealed in that specific transaction.
Routing and Network Topology
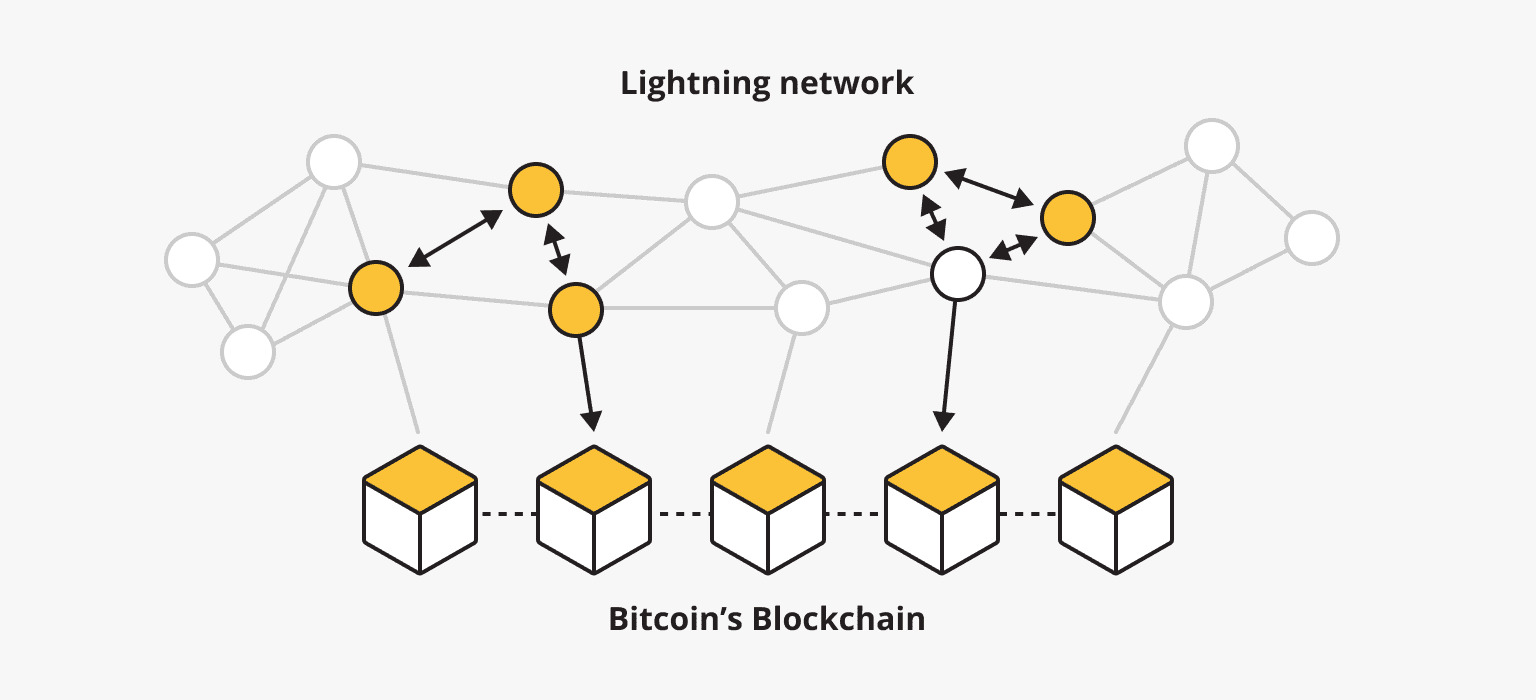
A Lightning node is software that connects and interacts with the underlying blockchain network and within the Lightning Network itself. The underlying blockchain network refers to any blockchain network implemented by the Lightning Network, such as Bitcoin and Litecoin.
Nodes in the Lightning Network differ from nodes in the Bitcoin network primarily in how they verify transactions. Bitcoin network nodes need to verify every transaction on the blockchain, whereas Lightning nodes only need to verify transactions that directly interact with them.
A Lightning node serves as a gateway into the Lightning Network. To explore the LN technology and leverage its benefits, operating at least one functioning node is necessary. Due to its decentralized nature, anyone can run a node regardless of which network they use.
Each channel in the network has a shared capacity, which is determined by the amount of Bitcoin allocated when creating the channel. This capacity may be under the control of one of the channel parties, affecting its ability to process payments. The total capacity of a channel is the sum of the local capacity of each analogous channel or the combined local and remote capacities of its own channel.
Due to the dynamic nature of the network, a route that successfully works for one payment may not work for the next one as balances shift and channels open or close. Therefore, a Bitcoin unit's path in the network can be unpredictable. However, various software tools are available to gain insights into capital allocation and movement within a node.
Running a routing node does not require highly specialized programming skills, an in-depth understanding of cryptography, or complex financial markets. However, it does require careful management and attention.
What is Lightning Wallet: Setting Up and Conducting Transactions
A Lightning wallet, also known as a Lightning Network wallet, is a type of digital wallet specifically designed for participating in the Lightning Network. A Lightning wallet allows users to receive and send Bitcoins through the Lightning Network, enabling faster and cheaper transactions than traditional on-chain transactions. This is achieved by creating payment channels between participants, through which transactions can be conducted off-chain, reducing the load on the Bitcoin blockchain.
Types of Lightning Wallets
- Custodial Wallets
Custodial Lightning wallets are managed by third parties, such as cryptocurrency exchanges. Examples of custodial wallets include Strike (by Zap), Wallet of Satoshi, BlueWallet (custodial mode), and Breez Wallet. These wallets offer convenience, but users must have complete trust in the third parties managing the wallets to ensure the security of their transactions.
- Non-custodial Wallets
Non-custodial Lightning wallets, also known as self-hosted wallets, give users full control over their funds and private keys. Examples of non-custodial wallets include Zap Wallet, Eclair Wallet, Phoenix Wallet, Zeus Wallet, and RTL (Ride The Lightning). These wallets are preferred by users who prioritize security and control, allowing them to independently manage their Lightning channels.
- Mobile Wallets
Mobile Lightning wallets are designed for smartphones and tablets. Examples of mobile wallets include BlueWallet (in non-custodial mode), Breez Wallet, Wallet of Satoshi, Eclair Wallet, and Zeus Wallet. Mobile wallets often have intuitive interfaces and can scan QR codes for convenient payment initiation.
- Desktop Wallets
Desktop Lightning wallets are software applications installed on personal computers or laptops, offering extensive features and advanced functionality. Examples of desktop wallets include Zap Wallet, Eclair Wallet, ThunderHub, Joule (a browser extension), and Electrum (with Lightning Network support). These wallets are preferred by users who require comprehensive control and management capabilities.
- Web Wallets
Web-based Lightning wallets operate through web browsers, providing users with access to their funds from any internet-connected device. Examples of web wallets include the Wallet of Satoshi, Tippin.me, Lightning Peach, Breez Wallet (web version), and Lightning Labs' Lightning Web Wallet.
- Hardware Wallets
Hardware wallets are physical devices specifically designed to secure private keys and facilitate cryptocurrency transactions. Some hardware wallets integrate with the Lightning Network, enabling autonomous management and secure transaction signing. Examples of hardware wallets with Lightning support include Trezor, Ledger, and Coldcard.
Opening a Payment Channel and Conducting Transactions
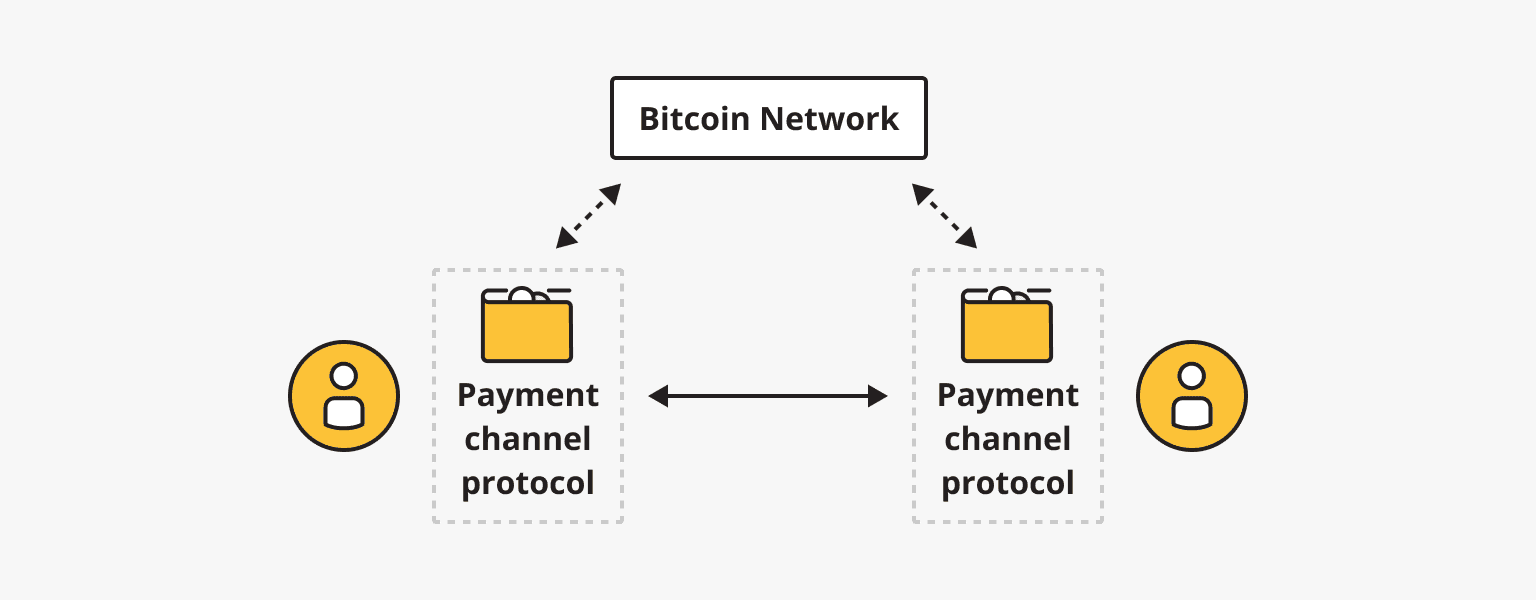
After creating and funding your Lightning wallet, you can start conducting transactions within the Lightning Network. Every transaction begins with the opening of a payment channel. Two parties must agree on the channel parameters to open a payment channel. The party funding the channel creates a funding transaction but does not broadcast it to the network. They also create a commitment transaction that allows them to reclaim their funds from the channel. The funding party then asks the second party also to sign the commitment transaction.
Once the commitment transaction is signed by the second party, the funding transaction can be broadcasted, and the payment channel is funded. However, the first party can only spend the funds with the consent of the second party. If the second party is unresponsive, the first party can broadcast the commitment transaction to unilaterally close the channel and reclaim its funds.
With an open payment channel, both parties can update their balances within the channel without involving the blockchain. They can send funds back and forth, creating and exchanging new commitment transactions that reflect the updated balances. These updates are known only to both parties and do not require on-chain transactions, enabling fast and low-cost transactions. With each payment, both parties invalidate each other's previous commitment transactions, ensuring that only the latest transaction can be used to settle the channel balance in case of a unilateral channel closure.
Regarding channel closure, there are two methods: cooperative and non-cooperative.
The parties agree on the final channel balance and closure conditions in a cooperative closure. They create and sign a new transaction that returns the funds from the channel back to their wallets. Once this transaction is confirmed on the blockchain, they can use the funds elsewhere or open new channels.
If one party is unresponsive or uncooperative, a non-cooperative closure, also known as forced closure, can occur. The initiating party can publish the latest commitment transaction on the blockchain, which sends their own funds to an arbitration contract. The funds of the other party are immediately returned to their wallet. This allows the non-initiating party to contest the forced closure.
If one party attempts to cheat by publishing an older commitment transaction, the other party can use the previously exchanged revocation key to reclaim the funds from the malicious actor. This serves as an incentive for both parties to remain honest and ensures network security.
Overall, payment channels allow parties to conduct frequent, fast, and cost-effective transactions off-chain while leveraging the security of the Bitcoin blockchain.
Managing Lightning Network Nodes
Running a Lightning node is essential to participating in the Lightning Network. Lightning nodes enable fast and low-cost transactions by creating payment channels and routing payments between nodes.
Setting up a Lightning Node
First, you'll need a virtual private server (VPS) or dedicated server to host your Lightning node. Choose a reliable hosting provider and install the necessary software, such as LND (Lightning Network Daemon) or c-lightning. Follow the installation instructions provided by your chosen Lightning Network implementation.
Managing Channels and Balancing
Once your node is up and running, you can create payment channels with other Lightning Network nodes. Channels allow users to conduct direct transactions with each other off-chain, reducing transaction fees and increasing transaction speed. Effective channel management is crucial for optimizing node performance. When managing channels, consider the following aspects:
- Open payment channels with nodes that have good connectivity, high liquidity, and low fees. This improves node connectivity and enhances its routing capabilities.
- Set appropriate channel capacity to balance your node's liquidity. Avoid opening channels with excessive or insufficient capacity, as it can impact routing efficiency.
- Regularly monitor channel balances. Imbalanced channels can limit your node's ability to route payments effectively.
- Close inefficient or unused channels to free up capital and improve routing efficiency.
Routing Fees and Node Revenue
As an operator of a Lightning node, you can generate income by charging routing fees for payments routed through your node. It is important to set the right fee policy to strike a balance between competitiveness and profitability. Consider the following factors:
- Define your fee structure based on the payment size, cost, and market conditions. You can charge a fixed fee or a percentage of the payment amount.
- Monitor the fee rates of other nodes to ensure the competitiveness of your fees. Charging excessively high fees may deter users from routing payments through your node.
- Maintain sufficient liquidity in your channels to facilitate routing. Nodes with good connectivity and high liquidity are more likely to receive routing requests, which increases your income.
Lightning Node Security

When managing a Lightning Network node, special attention should be given to security considerations. This will help protect your funds and ensure overall network security.
- Regularly update your Lightning node software. Stay informed about new releases and follow the official documentation provided by the software implementation you are using.
- Use a secure operating system for your node, such as a hardened Linux distribution, and keep it up to date. Disable unnecessary services and regularly check for vulnerabilities. How to choose a Linux distribution?
- For storing the private keys of your Lightning node, it is recommended to use a hardware wallet such as Trezor or Ledger. This provides an additional layer of security as the keys are stored in an offline environment and protected from potential malware or hacking attempts.
- Configure a firewall to restrict incoming and outgoing network connections to your Lightning node. Allow only necessary ports and IP addresses for communication with the node. Consider using a virtual private network (VPN) for added security. What are the benefits of a dedicated IP for a VPN?
- When opening channels, make sure to connect to well-established, reputable counterparts. Avoid connecting to nodes with a low reputation or unknown operators.
- Consider utilizing watchtower services. Watchtowers are third-party services that help monitor channels for potential breaches or attempted fraud.
By following these security practices, you can enhance the protection of your Lightning node and contribute to the overall security of the Lightning Network.
VPS
Choose the suitable configuration and enjoy all the benefits of a virtual private server.
From $4.99/moDedicated Server
Smooth operation, high performance, and user-friendly setup - it's all there for you.
From $9.99/mo